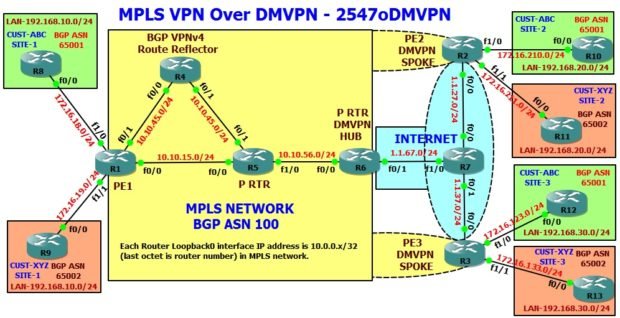
DMVPN Phase 3
The Shortcut Switching Enhancements for NHRP in DMVPN Phase 3 provides a more scalable alternative to the previous NHRP model. Routers in a Dynamic Multipoint VPN (DMVPN) Phase 3 network use Next Hop Resolution Protocol (NHRP) Shortcut Switching to discover shorter paths to a destination network after receiving an NHRP redirect message from the hub. This allows the routers to communicate directly with each other without the need for an intermediate hop.
Benefits of DMVPN Phase 3 Design:
- Allows summarization of routing protocol updates from hub to spokes. The spokes no longer need to have an individual route with an IP next-hop of the tunnel IP address of the remote spoke for the networks behind all the other spokes. The spokes can use summarized routes or specific routes with an IP next-hop of the tunnel IP address of the hub and still be able to build spoke-to-spoke tunnels.
- Allows for hierarchical (greater than one level) and more complex tree-based DMVPN network topologies. Tree-based topologies allow the capability to build DMVPN networks with regional hubs that are spokes of central hubs. This architecture
allows the regional hub to handle the data and NHRP control traffic for its regional spokes, but still allows spoke-to-spoke tunnels to be built between any spokes within the DMVPN network, whether they are in the same region or not. This architecture also allows the DMVPN network layout to more closely match regional or hierarchical data flow patterns.
Check these links for
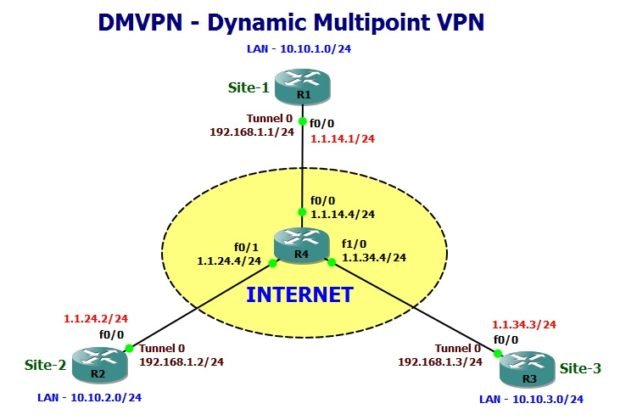
Here is the network topology for DMVPN phase 3 discussion and configuration.
The DMVPN Phase 2 design requires to maintain full routing table on all spoke routers. Each route for remote spoke networks needs to be a specific route with the next hop pointing to the remote spoke’s tunnel address. This prevents the hub from being able to send down a summarized route to the spokes for a more concise routing table.
Phase 3 overcomes this restriction using NHRP traffic indication messages from the hub to signal to the spokes that a better path exists to reach the target network. This functionality is enabled by configuring ip nhrp redirect on the hub and ip nhrp shortcut on the spokes. The redirect command tells the hub to send the NHRP traffic indication message while the shortcut command tells the spokes to accept the redirect and install the shortcut route.
DMVPN Phase 3 configuration with EIGRP
Configuration:
----------
R1 - Hub:
----------
hostname R1
!
ip cef
!
crypto isakmp policy 10
encr aes
authentication pre-share
group 2
crypto isakmp key DmVpNpR3$h@r3dK3Y address 0.0.0.0
!
!
crypto ipsec transform-set TRANSFORM-SET esp-aes esp-sha-hmac
mode transport
!
crypto ipsec profile PROTECT-GRE
set transform-set TRANSFORM-SET
!
interface Tunnel0
bandwidth 4096
ip address 192.168.1.1 255.255.255.0
no ip redirects
ip mtu 1400
ip nhrp authentication NhRp@UtH
ip nhrp map multicast dynamic
ip nhrp network-id 100
ip nhrp redirect
ip summary-address eigrp 100 10.10.0.0 255.255.0.0
ip tcp adjust-mss 1360
tunnel source FastEthernet0/0
tunnel mode gre multipoint
tunnel key 123
tunnel protection ipsec profile PROTECT-GRE
!
interface FastEthernet0/0
ip address 1.1.14.1 255.255.255.0
!
interface FastEthernet0/1
ip address 10.10.1.1 255.255.255.0
!
router eigrp 100
network 10.10.1.1 0.0.0.0
network 192.168.1.1 0.0.0.0
!
ip route 0.0.0.0 0.0.0.0 1.1.14.4
------------
R2 - Spoke:
------------
hostname R2
!
ip cef
!
crypto isakmp policy 10
encr aes
authentication pre-share
group 2
crypto isakmp key DmVpNpR3$h@r3dK3Y address 0.0.0.0
!
!
crypto ipsec transform-set TRANSFORM-SET esp-aes esp-sha-hmac
mode transport
!
crypto ipsec profile PROTECT-GRE
set transform-set TRANSFORM-SET
!
interface Tunnel0
bandwidth 4096
ip address 192.168.1.2 255.255.255.0
no ip redirects
ip mtu 1400
ip nhrp authentication NhRp@UtH
ip nhrp map multicast 1.1.14.1
ip nhrp map 192.168.1.1 1.1.14.1
ip nhrp network-id 100
ip nhrp nhs 192.168.1.1
ip nhrp shortcut
ip tcp adjust-mss 1360
tunnel source FastEthernet0/0
tunnel mode gre multipoint
tunnel key 123
tunnel protection ipsec profile PROTECT-GRE
!
interface FastEthernet0/0
ip address 1.1.24.2 255.255.255.0
!
interface FastEthernet0/1
ip address 10.10.2.2 255.255.255.0
!
router eigrp 100
network 10.10.2.2 0.0.0.0
network 192.168.1.2 0.0.0.0
!
ip route 0.0.0.0 0.0.0.0 1.1.24.4
------------
R3 - Spoke:
------------
hostname R3
!
ip cef
!
crypto isakmp policy 10
encr aes
authentication pre-share
group 2
crypto isakmp key DmVpNpR3$h@r3dK3Y address 0.0.0.0
!
!
crypto ipsec transform-set TRANSFORM-SET esp-aes esp-sha-hmac
mode transport
!
crypto ipsec profile PROTECT-GRE
set transform-set TRANSFORM-SET
!
interface Tunnel0
bandwidth 4096
ip address 192.168.1.3 255.255.255.0
no ip redirects
ip mtu 1400
ip nhrp authentication NhRp@UtH
ip nhrp map multicast 1.1.14.1
ip nhrp map 192.168.1.1 1.1.14.1
ip nhrp network-id 100
ip nhrp nhs 192.168.1.1
ip nhrp shortcut
ip tcp adjust-mss 1360
tunnel source FastEthernet0/0
tunnel mode gre multipoint
tunnel key 123
tunnel protection ipsec profile PROTECT-GRE
!
interface FastEthernet0/0
ip address 1.1.34.3 255.255.255.0
!
interface FastEthernet0/1
ip address 10.10.3.3 255.255.255.0
!
router eigrp 100
network 10.10.3.3 0.0.0.0
network 192.168.1.3 0.0.0.0
!
ip route 0.0.0.0 0.0.0.0 1.1.34.4
---------------
R4 - Internet:
---------------
hostname R4
!
interface FastEthernet0/0
ip address 1.1.14.4 255.255.255.0
!
interface FastEthernet0/1
ip address 1.1.24.4 255.255.255.0
!
interface FastEthernet1/0
ip address 1.1.34.4 255.255.255.0
!
Verification:
- Hub and Spokes routers are using mGRE tunnels
R1#show int t0
Tunnel0 is up, line protocol is up
Hardware is Tunnel
Internet address is 192.168.1.1/24
MTU 17870 bytes, BW 4096 Kbit/sec, DLY 50000 usec,
reliability 255/255, txload 1/255, rxload 1/255
Encapsulation TUNNEL, loopback not set
Keepalive not set
Tunnel source 1.1.14.1 (FastEthernet0/0)
Tunnel Subblocks:
src-track:
Tunnel0 source tracking subblock associated with FastEthernet0/0
Set of tunnels with source FastEthernet0/0, 1 member (includes iterators), on interface <OK>
Tunnel protocol/transport multi-GRE/IP
R2#show int t0
Tunnel0 is up, line protocol is up
Hardware is Tunnel
Internet address is 192.168.1.2/24
MTU 17870 bytes, BW 4096 Kbit/sec, DLY 50000 usec,
reliability 255/255, txload 1/255, rxload 1/255
Encapsulation TUNNEL, loopback not set
Keepalive not set
Tunnel source 1.1.24.2 (FastEthernet0/0)
Tunnel Subblocks:
src-track:
Tunnel0 source tracking subblock associated with FastEthernet0/0
Set of tunnels with source FastEthernet0/0, 1 member (includes iterators), on interface <OK>
Tunnel protocol/transport multi-GRE/IP
R3#show int t0
Tunnel0 is up, line protocol is up
Hardware is Tunnel
Internet address is 192.168.1.3/24
MTU 17870 bytes, BW 4096 Kbit/sec, DLY 50000 usec,
reliability 255/255, txload 1/255, rxload 1/255
Encapsulation TUNNEL, loopback not set
Keepalive not set
Tunnel source 1.1.34.3 (FastEthernet0/0)
Tunnel Subblocks:
src-track:
Tunnel0 source tracking subblock associated with FastEthernet0/0
Set of tunnels with source FastEthernet0/0, 1 member (includes iterators), on interface <OK>
Tunnel protocol/transport multi-GRE/IP
- Routing adjacencies (EIGRP neighborship) are between Hub and Spokes only
R1#show ip eigrp neighbors
EIGRP-IPv4 Neighbors for AS(100)
H Address Interface Hold Uptime SRTT RTO Q Seq
(sec) (ms) Cnt Num
1 192.168.1.2 Tu0 10 00:28:43 188 1128 0 3
0 192.168.1.3 Tu0 14 00:29:10 174 1044 0 3
R2#show ip eigrp neighbors
EIGRP-IPv4 Neighbors for AS(100)
H Address Interface Hold Uptime SRTT RTO Q Seq
(sec) (ms) Cnt Num
0 192.168.1.1 Tu0 14 00:28:45 1282 5000 0 5
R3#show ip eigrp neighbors
EIGRP-IPv4 Neighbors for AS(100)
H Address Interface Hold Uptime SRTT RTO Q Seq
(sec) (ms) Cnt Num
0 192.168.1.1 Tu0 11 00:29:16 200 1200 0 2
- Routing Table
- Hub router advertised a summary route (10.10.0.0/16) to spoke EIGRP routers
R1#show ip route eigrp | beg Gate
Gateway of last resort is 1.1.14.4 to network 0.0.0.0
10.0.0.0/8 is variably subnetted, 5 subnets, 3 masks
D 10.10.0.0/16 is a summary, 00:30:13, Null0
D 10.10.2.0/24 [90/1907456] via 192.168.1.2, 00:29:34, Tunnel0
D 10.10.3.0/24 [90/1907456] via 192.168.1.3, 00:30:04, Tunnel0
R2#show ip route eigrp | beg Gate
Gateway of last resort is 1.1.24.4 to network 0.0.0.0
10.0.0.0/8 is variably subnetted, 3 subnets, 3 masks
D 10.10.0.0/16 [90/1907456] via 192.168.1.1, 00:29:38, Tunnel0
R3#show ip route eigrp | beg Gate
Gateway of last resort is 1.1.34.4 to network 0.0.0.0
10.0.0.0/8 is variably subnetted, 3 subnets, 3 masks
D 10.10.0.0/16 [90/1907456] via 192.168.1.1, 00:30:10, Tunnel0
- DMVPN Status
- Initially there is no spoke-to-spoke communication
R1#show dmvpn
Legend: Attrb --> S - Static, D - Dynamic, I - Incomplete
N - NATed, L - Local, X - No Socket
# Ent --> Number of NHRP entries with same NBMA peer
NHS Status: E --> Expecting Replies, R --> Responding, W --> Waiting
UpDn Time --> Up or Down Time for a Tunnel
====================================================================
Interface: Tunnel0, IPv4 NHRP Details
Type:Hub, NHRP Peers:2,
# Ent Peer NBMA Addr Peer Tunnel Add State UpDn Tm Attrb
----- --------------- --------------- ----- -------- -----
1 1.1.24.2 192.168.1.2 UP 00:30:53 D
1 1.1.34.3 192.168.1.3 UP 00:31:22 D
R2#show dmvpn
Legend: Attrb --> S - Static, D - Dynamic, I - Incomplete
N - NATed, L - Local, X - No Socket
# Ent --> Number of NHRP entries with same NBMA peer
NHS Status: E --> Expecting Replies, R --> Responding, W --> Waiting
UpDn Time --> Up or Down Time for a Tunnel
======================================================================
Interface: Tunnel0, IPv4 NHRP Details
Type:Spoke, NHRP Peers:1,
# Ent Peer NBMA Addr Peer Tunnel Add State UpDn Tm Attrb
----- --------------- --------------- ----- -------- -----
1 1.1.14.1 192.168.1.1 UP 00:30:55 S
R3#show dmvpn
Legend: Attrb --> S - Static, D - Dynamic, I - Incomplete
N - NATed, L - Local, X - No Socket
# Ent --> Number of NHRP entries with same NBMA peer
NHS Status: E --> Expecting Replies, R --> Responding, W --> Waiting
UpDn Time --> Up or Down Time for a Tunnel
======================================================================
Interface: Tunnel0, IPv4 NHRP Details
Type:Spoke, NHRP Peers:1,
# Ent Peer NBMA Addr Peer Tunnel Add State UpDn Tm Attrb
----- --------------- --------------- ----- -------- -----
1 1.1.14.1 192.168.1.1 UP 00:31:26 S
- Traffic between Spoke R2 and Spoke R3
- First packet would traverse via Hub and it will trigger NHRP shortcut switching process then traffic will start using direct spoke-to-spoke tunnel
R2#trace 10.10.3.3 so 10.10.2.2
Type escape sequence to abort.
Tracing the route to 10.10.3.3
VRF info: (vrf in name/id, vrf out name/id)
1 192.168.1.1 132 msec 136 msec 160 msec << Hub R1 Tunnel IP
2 192.168.1.3 236 msec << Spoke R3 Tunnel IP
Following events occur for NHRP shortcut switching:
When the traffic between Spokes R2 & R3 arrives at Hub-R1 router, it will send redirect message (due to "ip nhrp redirect") to spokes to tell them, as both of you are DMVPN spokes and there would be a better path if you can build a direct spoke-to-spoke tunnel.
=> Hub-R1 sends NHRP redirect to Spoke-R2
R1#
*Mar 1 23:24:47.063: NHRP: Send Traffic Indication via Tunnel0 vrf 0, packet size: 100
*Mar 1 23:24:47.071: src: 192.168.1.1, dst: 10.10.2.2
*Mar 1 23:24:47.079: (F) afn: AF_IP(1), type: IP(800), hop: 255, ver: 1
*Mar 1 23:24:47.079: shtl: 4(NSAP), sstl: 0(NSAP)
*Mar 1 23:24:47.083: pktsz: 100 extoff: 68
*Mar 1 23:24:47.087: (M) traffic code: redirect(0)
*Mar 1 23:24:47.087: src NBMA: 1.1.14.1
*Mar 1 23:24:47.087: src protocol: 192.168.1.1, dst protocol: 10.10.2.2
*Mar 1 23:24:47.087: Contents of nhrp traffic indication packet:
*Mar 1 23:24:47.087: 45 00 00 64 00 00 00 00 FE 01 A3 80 0A 0A 02 02
*Mar 1 23:24:47.087: 0A 0A 03 03 08 00 A8 A1 00 00 00
=> Hub-R1 sends NHRP redirect to Spoke-R3
R1#
*Mar 1 23:24:47.139: NHRP: Send Traffic Indication via Tunnel0 vrf 0, packet size: 100
*Mar 1 23:24:47.143: src: 192.168.1.1, dst: 10.10.3.3
*Mar 1 23:24:47.151: (F) afn: AF_IP(1), type: IP(800), hop: 255, ver: 1
*Mar 1 23:24:47.155: shtl: 4(NSAP), sstl: 0(NSAP)
*Mar 1 23:24:47.155: pktsz: 100 extoff: 68
*Mar 1 23:24:47.159: (M) traffic code: redirect(0)
*Mar 1 23:24:47.163: src NBMA: 1.1.14.1
*Mar 1 23:24:47.163: src protocol: 192.168.1.1, dst protocol: 10.10.3.3
*Mar 1 23:24:47.171: Contents of nhrp traffic indication packet:
*Mar 1 23:24:47.175: 45 00 00 64 00 00 00 00 FE 01 A3 80 0A 0A 03 03
*Mar 1 23:24:47.179: 0A 0A 02 02 00 00 B0 A1 00 00 00
=> Spoke-R2 receives NHRP redirect from Hub-R1
R2#
*Mar 1 23:24:47.135: NHRP: Receive Traffic Indication via Tunnel0 vrf 0, packet size: 100
*Mar 1 23:24:47.139: (F) afn: AF_IP(1), type: IP(800), hop: 255, ver: 1
*Mar 1 23:24:47.139: shtl: 4(NSAP), sstl: 0(NSAP)
*Mar 1 23:24:47.139: pktsz: 100 extoff: 68
*Mar 1 23:24:47.139: (M) traffic code: redirect(0)
*Mar 1 23:24:47.139: src NBMA: 1.1.14.1
*Mar 1 23:24:47.143: src protocol: 192.168.1.1, dst protocol: 10.10.2.2
*Mar 1 23:24:47.143: Contents of nhrp traffic indication packet:
*Mar 1 23:24:47.143: 45 00 00 64 00 00 00 00 FE 01 A3 80 0A 0A 02 02
*Mar 1 23:24:47.143: 0A 0A 03 03 08 00 A8 A1 00 00 00
=> Spoke-R2 will accept this message and want to build a shortcut path (direct spoke-to-spoke tunnel) because of "ip nhrp shortcut" command.
=> Spoke-R2 will send a NHRP resolution request to Spoke-R3 via Hub-R1, to find NBMA IP of Spoke-R3 to build a direct spoke-to-spoke tunnel
R2#
*Mar 1 23:24:47.163: NHRP: Send Resolution Request via Tunnel0 vrf 0, packet size: 88
*Mar 1 23:24:47.167: src: 192.168.1.2, dst: 10.10.3.3
*Mar 1 23:24:47.167: (F) afn: AF_IP(1), type: IP(800), hop: 255, ver: 1
*Mar 1 23:24:47.167: shtl: 4(NSAP), sstl: 0(NSAP)
*Mar 1 23:24:47.167: pktsz: 88 extoff: 52
*Mar 1 23:24:47.167: (M) flags: "router auth src-stable nat ", reqid: 2
*Mar 1 23:24:47.167: src NBMA: 1.1.24.2
*Mar 1 23:24:47.167: src protocol: 192.168.1.2, dst protocol: 10.10.3.3
*Mar 1 23:24:47.167: (C-1) code: no error(0)
*Mar 1 23:24:47.167: prefix: 32, mtu: 17870, hd_time: 7200
*Mar 1 23:24:47.167: addr_len: 0(NSAP), subaddr_len: 0(NSAP), proto_len: 0, pref: 0
=> Similar events happens on Spoke-R3.
=> Spoke-R3 receives NHRP redirect from Hub-R1
=> Spoke-R3 will also send a NHRP resolution request to Spoke-R2 via Hub-R1, to find NBMA IP of Spoke-R2 to build a direct spoke-to-spoke tunnel
R3#
*Mar 1 23:24:47.263: NHRP: Receive Traffic Indication via Tunnel0 vrf 0, packet size: 100
*Mar 1 23:24:47.267: (F) afn: AF_IP(1), type: IP(800), hop: 255, ver: 1
*Mar 1 23:24:47.271: shtl: 4(NSAP), sstl: 0(NSAP)
*Mar 1 23:24:47.275: pktsz: 100 extoff: 68
*Mar 1 23:24:47.275: (M) traffic code: redirect(0)
*Mar 1 23:24:47.275: src NBMA: 1.1.14.1
*Mar 1 23:24:47.275: src protocol: 192.168.1.1, dst protocol: 10.10.3.3
*Mar 1 23:24:47.275: Contents of nhrp traffic indication packet:
*Mar 1 23:24:47.275: 45 00 00 64 00 00 00 00 FE 01 A3 80 0A 0A 03 03
*Mar 1 23:24:47.275: 0A 0A 02 02 00 00 B0 A1 00 00 00
R3#
*Mar 1 23:24:47.307: NHRP: Send Resolution Request via Tunnel0 vrf 0, packet size: 88
*Mar 1 23:24:47.311: src: 192.168.1.3, dst: 10.10.2.2
*Mar 1 23:24:47.319: (F) afn: AF_IP(1), type: IP(800), hop: 255, ver: 1
*Mar 1 23:24:47.323: shtl: 4(NSAP), sstl: 0(NSAP)
*Mar 1 23:24:47.323: pktsz: 88 extoff: 52
R3#*Mar 1 23:24:47.327: (M) flags: "router auth src-stable nat ", reqid: 2
*Mar 1 23:24:47.331: src NBMA: 1.1.34.3
*Mar 1 23:24:47.335: src protocol: 192.168.1.3, dst protocol: 10.10.2.2
*Mar 1 23:24:47.335: (C-1) code: no error(0)
*Mar 1 23:24:47.335: prefix: 32, mtu: 17870, hd_time: 7200
*Mar 1 23:24:47.335: addr_len: 0(NSAP), subaddr_len: 0(NSAP), proto_len: 0, pref: 0
=> Hub-R1 receives NHRP resolution requests and forward it to both the spokes (R2 & R3)
R1#
*Mar 1 23:24:47.211: NHRP: Receive Resolution Request via Tunnel0 vrf 0, packet size: 88
*Mar 1 23:24:47.219: (F) afn: AF_IP(1), type: IP(800), hop: 255, ver: 1
*Mar 1 23:24:47.219: shtl: 4(NSAP), sstl: 0(NSAP)
*Mar 1 23:24:47.219: pktsz: 88 extoff: 52
*Mar 1 23:24:47.219: (M) flags: "router auth src-stable nat ", reqid: 2
*Mar 1 23:24:47.219: src NBMA: 1.1.24.2
*Mar 1 23:24:47.219: src protocol: 192.168.1.2, dst protocol: 10.10.3.3
*Mar 1 23:24:47.219: (C-1) code: no error(0)
*Mar 1 23:24:47.219:
R1# prefix: 32, mtu: 17870, hd_time: 7200
*Mar 1 23:24:47.219: addr_len: 0(NSAP), subaddr_len: 0(NSAP), proto_len: 0, pref: 0
*Mar 1 23:24:47.223: NHRP: Forwarding Resolution Request via Tunnel0 vrf 0, packet size: 108
*Mar 1 23:24:47.223: src: 192.168.1.1, dst: 10.10.3.3
*Mar 1 23:24:47.223: (F) afn: AF_IP(1), type: IP(800), hop: 254, ver: 1
*Mar 1 23:24:47.223: shtl: 4(NSAP), sstl: 0(NSAP)
*Mar 1 23:24:47.223: pktsz: 108 extoff: 52
*Mar 1 23:24:47.223: (M) flags: "router auth src-stable nat ", reqid: 2
*Mar 1 23:24:47.223: src NBMA: 1.1.24.2
*Mar 1 23:24:47.223: src protocol: 192.168.1.2, dst protocol: 10.10.3.3
*Mar 1 23:24:47.223: (C-1) code: no error(0)
*Mar 1 23:24:47.223: prefix: 32, mtu: 17870, hd_time: 7200
*Mar 1 23:24:47.223: addr_len: 0(NSAP), subaddr_len: 0(NSAP), proto_len: 0, pref: 0
R1#
*Mar 1 23:24:47.387: NHRP: Receive Resolution Request via Tunnel0 vrf 0, packet size: 88
*Mar 1 23:24:47.395: (F)
R1# afn: AF_IP(1), type: IP(800), hop: 255, ver: 1
*Mar 1 23:24:47.399: shtl: 4(NSAP), sstl: 0(NSAP)
*Mar 1 23:24:47.399: pktsz: 88 extoff: 52
*Mar 1 23:24:47.403: (M) flags: "router auth src-stable nat ", reqid: 2
*Mar 1 23:24:47.403: src NBMA: 1.1.34.3
*Mar 1 23:24:47.403: src protocol: 192.168.1.3, dst protocol: 10.10.2.2
*Mar 1 23:24:47.403: (C-1) code: no error(0)
*Mar 1 23:24:47.403: prefix: 32, mtu: 17870, hd_time: 7200
*Mar 1 23:24:47.403: addr_len: 0(NSAP), subaddr_len: 0(NSAP), proto_len: 0, pref: 0
*Mar 1 23:24:47.407: NHRP: Forwarding Resolution Request via Tunnel0 vrf 0, packet size: 108
*Mar 1 23:24:47.407: src: 192.168.1.1, dst: 10.10.2.2
*Mar 1 23:24:47.407: (F) afn: AF_IP(1), type: IP(800), hop: 254, ver: 1
*Mar 1 23:24:47.407: shtl: 4(NSAP), sstl: 0(NSAP)
*Mar 1 23:24:47.407: pktsz: 108 extoff: 52
*Mar 1 23:24:47.407: (M) flags: "router auth src-stable nat ", reqid: 2
*Mar 1 23:24:47.407: src NBMA: 1.1.34.3
*Mar 1 23:24:47.407: src protocol: 192.168.1.3, dst protocol: 10.10.2.2
*Mar 1 23:24:47.407: (C-1) code: no error(0)
*Mar 1 23:24:47.407: prefix: 32, mtu: 17870, hd_time: 7200
*Mar 1 23:24:47.407: addr_len: 0(NSAP), subaddr_len: 0(NSAP), proto_len: 0, pref: 0
=> Both Spoke-R2 & Spoke-R3 send NHRP resolution reply via Hub-R1
R2#
*Mar 1 23:24:48.431: NHRP: Send Resolution Reply via Tunnel0 vrf 0, packet size: 136
*Mar 1 23:24:48.435: src: 192.168.1.2, dst: 192.168.1.3
R3#
*Mar 1 23:24:48.267: NHRP: Send Resolution Reply via Tunnel0 vrf 0, packet size: 136
*Mar 1 23:24:48.271: src: 192.168.1.3, dst: 192.168.1.2
=> Finally, both Spokes receives each other's NHRP resolution reply
R2#
*Mar 1 23:24:48.311: NHRP: Receive Resolution Reply via Tunnel0 vrf 0, packet size: 136
*Mar 1 23:24:48.319: (F) afn: AF_IP(1), type: IP(800), hop: 255, ver: 1
*Mar 1 23:24:48.323: shtl: 4(NSAP), sstl: 0(NSAP)
*Mar 1 23:24:48.323: pktsz: 136 extoff: 60
*Mar 1 23:24:48.327: (M) flags: "router auth dst-stable unique src-stable nat ", reqid: 2
*Mar 1 23:24:48.331: src NBMA: 1.1.24.2
*Mar 1 23:24:48.335: src protocol: 192.168.1.2, dst protocol: 10.10.3.3
*Mar 1 23:24:48.335: (C-1) code: no error(0)
*Mar 1 23:24:48.335: prefix: 24, mtu: 17870, hd_time: 7199
*Mar 1 23:24:48.335: addr_len: 4(NSAP), subaddr_len: 0(NSAP), proto_len: 4, pref: 0
*Mar 1 23:24:48.335: client NBMA: 1.1.34.3
*Mar 1 23:24:48.335: client protocol: 192.168.1.3
R3#
*Mar 1 23:24:48.551: NHRP: Receive Resolution Reply via Tunnel0 vrf 0, packet size: 136
*Mar 1 23:24:48.559: (F) afn: AF_IP(1), type: IP(800), hop: 255, ver: 1
*Mar 1 23:24:48.563: shtl: 4(NSAP), sstl: 0(NSAP)
*Mar 1 23:24:48.563: pktsz: 136 extoff: 60
*Mar 1 23:24:48.567: (M) flags: "router auth dst-stable unique src-stable nat ", reqid: 2
*Mar 1 23:24:48.571: src NBMA: 1.1.34.3
*Mar 1 23:24:48.575: src protocol: 192.168.1.3, dst protocol: 10.10.2.2
*Mar 1 23:24:48.579: (C-1) code: no error(0)
*Mar 1 23:24:48.579: prefix: 24, mtu: 17870, hd_time: 7200
*Mar 1 23:24:48.579: addr_len: 4(NSAP), subaddr_len: 0(NSAP), proto_len: 4, pref: 0
*Mar 1 23:24:48.579: client NBMA: 1.1.24.2
*Mar 1 23:24:48.579: client protocol: 192.168.1.2
=> Now both spokes know each other's NBMA & Tunnel IP address, and can build a direct spoke-to-spoke tunnel
=> And both spokes add a NHRP shortcut route entry to reach each other's LAN subnet
R2#
*Mar 1 23:24:48.455: NHRP: Adding route entry for 10.10.3.0/24 to RIB
*Mar 1 23:24:48.455: NHRP: Route addition to RIB Successful
R3#
*Mar 1 23:24:48.587: NHRP: Adding route entry for 10.10.2.0/24 to RIB
*Mar 1 23:24:48.595: NHRP: Route addition to RIB Successful
- Let's test communication between Spoke-R2 and Spoke-R3 now
R2#ping 10.10.3.3 so 10.10.2.2
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.10.3.3, timeout is 2 seconds:
Packet sent with a source address of 10.10.2.2
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 116/136/152 ms
- Now traffic between Spoke-R2 and Spoke-R3 is using direct DMVPN tunnel
R2#trace 10.10.3.3 so 10.10.2.2
Type escape sequence to abort.
Tracing the route to 10.10.3.3
VRF info: (vrf in name/id, vrf out name/id)
1 192.168.1.3 148 msec * 116 msec << Spoke-R3 Tunnel IP
- Spokes routing table would show a new NHRP routing entry to reach subnet behind other spoke router
R2#show ip route
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
o - ODR, P - periodic downloaded static route, H - NHRP, l - LISP
+ - replicated route, % - next hop override
Gateway of last resort is 1.1.24.4 to network 0.0.0.0
S* 0.0.0.0/0 [1/0] via 1.1.24.4
1.0.0.0/8 is variably subnetted, 2 subnets, 2 masks
C 1.1.24.0/24 is directly connected, FastEthernet0/0
L 1.1.24.2/32 is directly connected, FastEthernet0/0
10.0.0.0/8 is variably subnetted, 4 subnets, 3 masks
D 10.10.0.0/16 [90/1907456] via 192.168.1.1, 01:31:44, Tunnel0
C 10.10.2.0/24 is directly connected, FastEthernet0/1
L 10.10.2.2/32 is directly connected, FastEthernet0/1
H 10.10.3.0/24 [250/1] via 192.168.1.3, 00:05:13, Tunnel0
192.168.1.0/24 is variably subnetted, 2 subnets, 2 masks
C 192.168.1.0/24 is directly connected, Tunnel0
L 192.168.1.2/32 is directly connected, Tunnel0
R3#show ip route
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
o - ODR, P - periodic downloaded static route, H - NHRP, l - LISP
+ - replicated route, % - next hop override
Gateway of last resort is 1.1.34.4 to network 0.0.0.0
S* 0.0.0.0/0 [1/0] via 1.1.34.4
1.0.0.0/8 is variably subnetted, 2 subnets, 2 masks
C 1.1.34.0/24 is directly connected, FastEthernet0/0
L 1.1.34.3/32 is directly connected, FastEthernet0/0
10.0.0.0/8 is variably subnetted, 4 subnets, 3 masks
D 10.10.0.0/16 [90/1907456] via 192.168.1.1, 01:32:12, Tunnel0
H 10.10.2.0/24 [250/1] via 192.168.1.2, 00:06:01, Tunnel0
C 10.10.3.0/24 is directly connected, FastEthernet0/1
L 10.10.3.3/32 is directly connected, FastEthernet0/1
192.168.1.0/24 is variably subnetted, 2 subnets, 2 masks
C 192.168.1.0/24 is directly connected, Tunnel0
L 192.168.1.3/32 is directly connected, Tunnel0
- DMVPN Status
R1#show dmvpn
Legend: Attrb --> S - Static, D - Dynamic, I - Incomplete
N - NATed, L - Local, X - No Socket
# Ent --> Number of NHRP entries with same NBMA peer
NHS Status: E --> Expecting Replies, R --> Responding, W --> Waiting
UpDn Time --> Up or Down Time for a Tunnel
======================================================================
Interface: Tunnel0, IPv4 NHRP Details
Type:Hub, NHRP Peers:2,
# Ent Peer NBMA Addr Peer Tunnel Add State UpDn Tm Attrb
----- --------------- --------------- ----- -------- -----
1 1.1.24.2 192.168.1.2 UP 01:37:55 D
1 1.1.34.3 192.168.1.3 UP 01:37:36 D
R2#show dmvpn
Legend: Attrb --> S - Static, D - Dynamic, I - Incomplete
N - NATed, L - Local, X - No Socket
# Ent --> Number of NHRP entries with same NBMA peer
NHS Status: E --> Expecting Replies, R --> Responding, W --> Waiting
UpDn Time --> Up or Down Time for a Tunnel
======================================================================
Interface: Tunnel0, IPv4 NHRP Details
Type:Spoke, NHRP Peers:2,
# Ent Peer NBMA Addr Peer Tunnel Add State UpDn Tm Attrb
----- --------------- --------------- ----- -------- -----
2 1.1.34.3 192.168.1.3 UP 00:11:26 DT1
192.168.1.3 UP 00:11:26 D
1 1.1.14.1 192.168.1.1 UP 01:37:59 S
*T1 - Route Installed
R3#show dmvpn
Legend: Attrb --> S - Static, D - Dynamic, I - Incomplete
N - NATed, L - Local, X - No Socket
# Ent --> Number of NHRP entries with same NBMA peer
NHS Status: E --> Expecting Replies, R --> Responding, W --> Waiting
UpDn Time --> Up or Down Time for a Tunnel
======================================================================
Interface: Tunnel0, IPv4 NHRP Details
Type:Spoke, NHRP Peers:2,
# Ent Peer NBMA Addr Peer Tunnel Add State UpDn Tm Attrb
----- --------------- --------------- ----- -------- -----
2 1.1.24.2 192.168.1.2 UP 00:11:29 DT1
192.168.1.2 UP 00:11:29 D
1 1.1.14.1 192.168.1.1 UP 01:37:43 S
*T1 - Route Installed
- NHRP Table
R1#show ip nhrp
192.168.1.2/32 via 192.168.1.2
Tunnel0 created 01:38:52, expire 01:41:01
Type: dynamic, Flags: unique registered used
NBMA address: 1.1.24.2
192.168.1.3/32 via 192.168.1.3
Tunnel0 created 01:38:33, expire 01:41:00
Type: dynamic, Flags: unique registered used
NBMA address: 1.1.34.3
R2#show ip nhrp
10.10.2.0/24 via 192.168.1.2
Tunnel0 created 00:12:24, expire 01:47:35
Type: dynamic, Flags: router unique local
NBMA address: 1.1.24.2
(no-socket)
10.10.3.0/24 via 192.168.1.3
Tunnel0 created 00:12:24, expire 01:47:35
Type: dynamic, Flags: router used rib
NBMA address: 1.1.34.3
192.168.1.1/32 via 192.168.1.1
Tunnel0 created 01:39:13, never expire
Type: static, Flags: used
NBMA address: 1.1.14.1
192.168.1.3/32 via 192.168.1.3
Tunnel0 created 00:12:25, expire 01:47:35
Type: dynamic, Flags: router implicit used
NBMA address: 1.1.34.3
R3#show ip nhrp
10.10.2.0/24 via 192.168.1.2
Tunnel0 created 00:12:26, expire 01:47:33
Type: dynamic, Flags: router used rib
NBMA address: 1.1.24.2
10.10.3.0/24 via 192.168.1.3
Tunnel0 created 00:12:26, expire 01:47:33
Type: dynamic, Flags: router unique local
NBMA address: 1.1.34.3
(no-socket)
192.168.1.1/32 via 192.168.1.1
Tunnel0 created 01:39:16, never expire
Type: static, Flags: used
NBMA address: 1.1.14.1
192.168.1.2/32 via 192.168.1.2
Tunnel0 created 00:12:27, expire 01:47:33
Type: dynamic, Flags: router implicit used
NBMA address: 1.1.24.2
DMVPN Phase 3 configuration with OSPF
- Tunnel mode mGRE on Hub and Spoke routers
- OSPF network type would be point-to-multipoint on Hub and Spoke Routers
- Route summarization is not feasible in single OSPF area, this is one of the main reason that OSPF is not an ideal routing protocol for DMVPN phase 3 designs
- Shortcut route is marked with “%” symbol which indicates next-hop override feature. It means router is not using next-hop IP from OSPF RIB entry, instead it is using DMVPN tunnel IP of remote spoke to route traffic over direct DMVPN tunnel.
Configuration:
----------
R1 - Hub:
----------
hostname R1
!
ip cef
!
crypto isakmp policy 10
encr aes
authentication pre-share
group 2
crypto isakmp key DmVpNpR3$h@r3dK3Y address 0.0.0.0
!
!
crypto ipsec transform-set TRANSFORM-SET esp-aes esp-sha-hmac
mode transport
!
crypto ipsec profile PROTECT-GRE
set transform-set TRANSFORM-SET
!
interface Tunnel0
bandwidth 4096
ip address 192.168.1.1 255.255.255.0
no ip redirects
ip mtu 1400
ip nhrp authentication NhRp@UtH
ip nhrp map multicast dynamic
ip nhrp network-id 100
ip nhrp redirect
ip tcp adjust-mss 1360
ip ospf network point-to-multipoint
tunnel source FastEthernet0/0
tunnel mode gre multipoint
tunnel key 123
tunnel protection ipsec profile PROTECT-GRE
!
interface FastEthernet0/0
ip address 1.1.14.1 255.255.255.0
!
interface FastEthernet0/1
ip address 10.10.1.1 255.255.255.0
!
router ospf 1
network 10.10.1.1 0.0.0.0 area 0
network 192.168.1.1 0.0.0.0 area 0
!
ip route 0.0.0.0 0.0.0.0 1.1.14.4
------------
R2 - Spoke:
------------
hostname R2
!
ip cef
!
crypto isakmp policy 10
encr aes
authentication pre-share
group 2
crypto isakmp key DmVpNpR3$h@r3dK3Y address 0.0.0.0
!
!
crypto ipsec transform-set TRANSFORM-SET esp-aes esp-sha-hmac
mode transport
!
crypto ipsec profile PROTECT-GRE
set transform-set TRANSFORM-SET
!
interface Tunnel0
bandwidth 4096
ip address 192.168.1.2 255.255.255.0
no ip redirects
ip mtu 1400
ip nhrp authentication NhRp@UtH
ip nhrp map multicast 1.1.14.1
ip nhrp map 192.168.1.1 1.1.14.1
ip nhrp network-id 100
ip nhrp nhs 192.168.1.1
ip nhrp shortcut
ip tcp adjust-mss 1360
ip ospf network point-to-multipoint
tunnel source FastEthernet0/0
tunnel mode gre multipoint
tunnel key 123
tunnel protection ipsec profile PROTECT-GRE
!
interface FastEthernet0/0
ip address 1.1.24.2 255.255.255.0
!
interface FastEthernet0/1
ip address 10.10.2.2 255.255.255.0
!
router ospf 1
network 10.10.2.2 0.0.0.0 area 0
network 192.168.1.2 0.0.0.0 area 0
!
ip route 0.0.0.0 0.0.0.0 1.1.24.4
------------
R3 - Spoke:
------------
hostname R3
!
ip cef
!
crypto isakmp policy 10
encr aes
authentication pre-share
group 2
crypto isakmp key DmVpNpR3$h@r3dK3Y address 0.0.0.0
!
!
crypto ipsec transform-set TRANSFORM-SET esp-aes esp-sha-hmac
mode transport
!
crypto ipsec profile PROTECT-GRE
set transform-set TRANSFORM-SET
!
interface Tunnel0
bandwidth 4096
ip address 192.168.1.3 255.255.255.0
no ip redirects
ip mtu 1400
ip nhrp authentication NhRp@UtH
ip nhrp map multicast 1.1.14.1
ip nhrp map 192.168.1.1 1.1.14.1
ip nhrp network-id 100
ip nhrp nhs 192.168.1.1
ip nhrp shortcut
ip tcp adjust-mss 1360
ip ospf network point-to-multipoint
tunnel source FastEthernet0/0
tunnel mode gre multipoint
tunnel key 123
tunnel protection ipsec profile PROTECT-GRE
!
interface FastEthernet0/0
ip address 1.1.34.3 255.255.255.0
!
interface FastEthernet0/1
ip address 10.10.3.3 255.255.255.0
!
router ospf 1
network 10.10.3.3 0.0.0.0 area 0
network 192.168.1.3 0.0.0.0 area 0
!
ip route 0.0.0.0 0.0.0.0 1.1.34.4
Verification:
- Tunnel OSPF Network Type
R1#show ip ospf int t0
Tunnel0 is up, line protocol is up
Internet Address 192.168.1.1/24, Area 0, Attached via Network Statement
Process ID 1, Router ID 192.168.1.1, Network Type POINT_TO_MULTIPOINT, Cost: 24
Topology-MTID Cost Disabled Shutdown Topology Name
0 24 no no Base
Transmit Delay is 1 sec, State POINT_TO_MULTIPOINT
Timer intervals configured, Hello 30, Dead 120, Wait 120, Retransmit 5
oob-resync timeout 120
Hello due in 00:00:19
Supports Link-local Signaling (LLS)
Cisco NSF helper support enabled
IETF NSF helper support enabled
Index 2/2, flood queue length 0
Next 0x0(0)/0x0(0)
Last flood scan length is 1, maximum is 1
Last flood scan time is 4 msec, maximum is 4 msec
Neighbor Count is 2, Adjacent neighbor count is 2
Adjacent with neighbor 192.168.1.3
Adjacent with neighbor 192.168.1.2
Suppress hello for 0 neighbor(s)
R2#show ip ospf int t0
Tunnel0 is up, line protocol is up
Internet Address 192.168.1.2/24, Area 0, Attached via Network Statement
Process ID 1, Router ID 192.168.1.2, Network Type POINT_TO_MULTIPOINT, Cost: 24
Topology-MTID Cost Disabled Shutdown Topology Name
0 24 no no Base
Transmit Delay is 1 sec, State POINT_TO_MULTIPOINT
Timer intervals configured, Hello 30, Dead 120, Wait 120, Retransmit 5
oob-resync timeout 120
Hello due in 00:00:15
Supports Link-local Signaling (LLS)
Cisco NSF helper support enabled
IETF NSF helper support enabled
Index 2/2, flood queue length 0
Next 0x0(0)/0x0(0)
Last flood scan length is 1, maximum is 1
Last flood scan time is 0 msec, maximum is 4 msec
Neighbor Count is 1, Adjacent neighbor count is 1
Adjacent with neighbor 192.168.1.1
Suppress hello for 0 neighbor(s)
R3#show ip ospf int t0
Tunnel0 is up, line protocol is up
Internet Address 192.168.1.3/24, Area 0, Attached via Network Statement
Process ID 1, Router ID 192.168.1.3, Network Type POINT_TO_MULTIPOINT, Cost: 24
Topology-MTID Cost Disabled Shutdown Topology Name
0 24 no no Base
Transmit Delay is 1 sec, State POINT_TO_MULTIPOINT
Timer intervals configured, Hello 30, Dead 120, Wait 120, Retransmit 5
oob-resync timeout 120
Hello due in 00:00:09
Supports Link-local Signaling (LLS)
Cisco NSF helper support enabled
IETF NSF helper support enabled
Index 2/2, flood queue length 0
Next 0x0(0)/0x0(0)
Last flood scan length is 1, maximum is 1
Last flood scan time is 4 msec, maximum is 4 msec
Neighbor Count is 1, Adjacent neighbor count is 1
Adjacent with neighbor 192.168.1.1
Suppress hello for 0 neighbor(s)
- OSPF Adjacencies
R1#show ip ospf neighbor
Neighbor ID Pri State Dead Time Address Interface
192.168.1.3 0 FULL/ - 00:01:37 192.168.1.3 Tunnel0
192.168.1.2 0 FULL/ - 00:01:55 192.168.1.2 Tunnel0
R2#show ip ospf neighbor
Neighbor ID Pri State Dead Time Address Interface
192.168.1.1 0 FULL/ - 00:01:50 192.168.1.1 Tunnel0
R3#show ip ospf neighbor
Neighbor ID Pri State Dead Time Address Interface
192.168.1.1 0 FULL/ - 00:01:48 192.168.1.1 Tunnel0
- Traffic between Spoke-R2 and Spoke-R3 is via direct spoke-to-spoke DMVPN tunnel
R2#ping 10.10.3.3 so 10.10.2.2
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.10.3.3, timeout is 2 seconds:
Packet sent with a source address of 10.10.2.2
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 120/134/148 ms
R2#trace 10.10.3.3 so 10.10.2.2
Type escape sequence to abort.
Tracing the route to 10.10.3.3
VRF info: (vrf in name/id, vrf out name/id)
1 192.168.1.3 128 msec * 152 msec << Spoke-R3 Tunnel IP
- DMVPN Status
R1#show dmvpn
Legend: Attrb --> S - Static, D - Dynamic, I - Incomplete
N - NATed, L - Local, X - No Socket
# Ent --> Number of NHRP entries with same NBMA peer
NHS Status: E --> Expecting Replies, R --> Responding, W --> Waiting
UpDn Time --> Up or Down Time for a Tunnel
======================================================================
Interface: Tunnel0, IPv4 NHRP Details
Type:Hub, NHRP Peers:2,
# Ent Peer NBMA Addr Peer Tunnel Add State UpDn Tm Attrb
----- --------------- --------------- ----- -------- -----
1 1.1.24.2 192.168.1.2 UP 01:33:58 D
1 1.1.34.3 192.168.1.3 UP 01:33:48 D
R2#show dmvpn
Legend: Attrb --> S - Static, D - Dynamic, I - Incomplete
N - NATed, L - Local, X - No Socket
# Ent --> Number of NHRP entries with same NBMA peer
NHS Status: E --> Expecting Replies, R --> Responding, W --> Waiting
UpDn Time --> Up or Down Time for a Tunnel
======================================================================
Interface: Tunnel0, IPv4 NHRP Details
Type:Spoke, NHRP Peers:2,
# Ent Peer NBMA Addr Peer Tunnel Add State UpDn Tm Attrb
----- --------------- --------------- ----- -------- -----
2 1.1.34.3 192.168.1.3 UP 00:01:42 DT2
192.168.1.3 UP 00:01:42 D
1 1.1.14.1 192.168.1.1 UP 01:34:01 S
*T2 - Nexthop-override
R3#show dmvpn
Legend: Attrb --> S - Static, D - Dynamic, I - Incomplete
N - NATed, L - Local, X - No Socket
# Ent --> Number of NHRP entries with same NBMA peer
NHS Status: E --> Expecting Replies, R --> Responding, W --> Waiting
UpDn Time --> Up or Down Time for a Tunnel
======================================================================
Interface: Tunnel0, IPv4 NHRP Details
Type:Spoke, NHRP Peers:2,
# Ent Peer NBMA Addr Peer Tunnel Add State UpDn Tm Attrb
----- --------------- --------------- ----- -------- -----
2 1.1.24.2 192.168.1.2 UP 00:01:44 DT2
192.168.1.2 UP 00:01:44 D
1 1.1.14.1 192.168.1.1 UP 01:33:54 S
*T2 - Nexthop-override
- Routing Table
R1#show ip route
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
o - ODR, P - periodic downloaded static route, H - NHRP, l - LISP
+ - replicated route, % - next hop override
Gateway of last resort is 1.1.14.4 to network 0.0.0.0
S* 0.0.0.0/0 [1/0] via 1.1.14.4
1.0.0.0/8 is variably subnetted, 2 subnets, 2 masks
C 1.1.14.0/24 is directly connected, FastEthernet0/0
L 1.1.14.1/32 is directly connected, FastEthernet0/0
10.0.0.0/8 is variably subnetted, 4 subnets, 2 masks
C 10.10.1.0/24 is directly connected, FastEthernet0/1
L 10.10.1.1/32 is directly connected, FastEthernet0/1
O 10.10.2.0/24 [110/25] via 192.168.1.2, 01:36:33, Tunnel0
O 10.10.3.0/24 [110/25] via 192.168.1.3, 01:36:03, Tunnel0
192.168.1.0/24 is variably subnetted, 4 subnets, 2 masks
C 192.168.1.0/24 is directly connected, Tunnel0
L 192.168.1.1/32 is directly connected, Tunnel0
O 192.168.1.2/32 [110/24] via 192.168.1.2, 01:36:33, Tunnel0
O 192.168.1.3/32 [110/24] via 192.168.1.3, 01:36:03, Tunnel0
R2#show ip route
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
o - ODR, P - periodic downloaded static route, H - NHRP, l - LISP
+ - replicated route, % - next hop override
Gateway of last resort is 1.1.24.4 to network 0.0.0.0
S* 0.0.0.0/0 [1/0] via 1.1.24.4
1.0.0.0/8 is variably subnetted, 2 subnets, 2 masks
C 1.1.24.0/24 is directly connected, FastEthernet0/0
L 1.1.24.2/32 is directly connected, FastEthernet0/0
10.0.0.0/8 is variably subnetted, 4 subnets, 2 masks
O 10.10.1.0/24 [110/25] via 192.168.1.1, 01:36:38, Tunnel0
C 10.10.2.0/24 is directly connected, FastEthernet0/1
L 10.10.2.2/32 is directly connected, FastEthernet0/1
O % 10.10.3.0/24 [110/49] via 192.168.1.1, 01:35:58, Tunnel0
192.168.1.0/24 is variably subnetted, 4 subnets, 2 masks
C 192.168.1.0/24 is directly connected, Tunnel0
O 192.168.1.1/32 [110/24] via 192.168.1.1, 01:36:38, Tunnel0
L 192.168.1.2/32 is directly connected, Tunnel0
O 192.168.1.3/32 [110/48] via 192.168.1.1, 01:35:58, Tunnel0
R3#show ip route
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
o - ODR, P - periodic downloaded static route, H - NHRP, l - LISP
+ - replicated route, % - next hop override
Gateway of last resort is 1.1.34.4 to network 0.0.0.0
S* 0.0.0.0/0 [1/0] via 1.1.34.4
1.0.0.0/8 is variably subnetted, 2 subnets, 2 masks
C 1.1.34.0/24 is directly connected, FastEthernet0/0
L 1.1.34.3/32 is directly connected, FastEthernet0/0
10.0.0.0/8 is variably subnetted, 4 subnets, 2 masks
O 10.10.1.0/24 [110/25] via 192.168.1.1, 01:36:10, Tunnel0
O % 10.10.2.0/24 [110/49] via 192.168.1.1, 01:36:10, Tunnel0
C 10.10.3.0/24 is directly connected, FastEthernet0/1
L 10.10.3.3/32 is directly connected, FastEthernet0/1
192.168.1.0/24 is variably subnetted, 4 subnets, 2 masks
C 192.168.1.0/24 is directly connected, Tunnel0
O 192.168.1.1/32 [110/24] via 192.168.1.1, 01:36:10, Tunnel0
O 192.168.1.2/32 [110/48] via 192.168.1.1, 01:36:10, Tunnel0
L 192.168.1.3/32 is directly connected, Tunnel0
- NHRP Table
R1#show ip nhrp
192.168.1.2/32 via 192.168.1.2
Tunnel0 created 01:45:40, expire 01:33:54
Type: dynamic, Flags: unique registered used
NBMA address: 1.1.24.2
192.168.1.3/32 via 192.168.1.3
Tunnel0 created 01:45:30, expire 01:33:54
Type: dynamic, Flags: unique registered used
NBMA address: 1.1.34.3
R2#show ip nhrp
10.10.2.0/24 via 192.168.1.2
Tunnel0 created 00:13:24, expire 01:46:35
Type: dynamic, Flags: router unique local
NBMA address: 1.1.24.2
(no-socket)
10.10.3.0/24 via 192.168.1.3
Tunnel0 created 00:13:23, expire 01:46:36
Type: dynamic, Flags: router used rib nho << next-hop override
NBMA address: 1.1.34.3
192.168.1.1/32 via 192.168.1.1
Tunnel0 created 01:46:18, never expire
Type: static, Flags: used
NBMA address: 1.1.14.1
192.168.1.3/32 via 192.168.1.3
Tunnel0 created 00:13:24, expire 01:46:35
Type: dynamic, Flags: router implicit
NBMA address: 1.1.34.3
R3#show ip nhrp
10.10.2.0/24 via 192.168.1.2
Tunnel0 created 00:13:30, expire 01:46:28
Type: dynamic, Flags: router used rib nho << next-hop override
NBMA address: 1.1.24.2
10.10.3.0/24 via 192.168.1.3
Tunnel0 created 00:13:30, expire 01:46:29
Type: dynamic, Flags: router unique local
NBMA address: 1.1.34.3
(no-socket)
192.168.1.1/32 via 192.168.1.1
Tunnel0 created 01:46:24, never expire
Type: static, Flags: used
NBMA address: 1.1.14.1
192.168.1.2/32 via 192.168.1.2
Tunnel0 created 00:13:31, expire 01:46:29
Type: dynamic, Flags: router implicit
NBMA address: 1.1.24.2
DMVPN Phase 3 configuration with BGP
- Hub and Spoke routers are using mGRE tunnels
- Hub router(s) act as route-reflector server(s)
- Spoke routers are route-reflector clients
- Hub router can send summary route to Spoke routers
- eBGP can also be used by configuring Hub and Spokes in different ASNs. Here we are using iBGP with route-reflector
Configuration:
----------
R1 - Hub:
----------
hostname R1
!
ip cef
!
crypto isakmp policy 10
encr aes
authentication pre-share
group 2
crypto isakmp key DmVpNpR3$h@r3dK3Y address 0.0.0.0
!
crypto ipsec transform-set TRANSFORM-SET esp-aes esp-sha-hmac
mode transport
!
crypto ipsec profile PROTECT-GRE
set transform-set TRANSFORM-SET
!
interface Tunnel0
bandwidth 4096
ip address 192.168.1.1 255.255.255.0
no ip redirects
ip mtu 1400
ip nhrp authentication NhRp@UtH
ip nhrp map multicast dynamic
ip nhrp network-id 100
ip nhrp redirect
ip tcp adjust-mss 1360
tunnel source FastEthernet0/0
tunnel mode gre multipoint
tunnel key 123
tunnel protection ipsec profile PROTECT-GRE
!
interface FastEthernet0/0
ip address 1.1.14.1 255.255.255.0
!
interface FastEthernet0/1
ip address 10.10.1.1 255.255.255.0
!
router bgp 65001
bgp router-id 192.168.1.1
bgp log-neighbor-changes
bgp listen range 192.168.1.0/24 peer-group DMVPN-SPOKES
bgp listen limit 50
network 10.10.1.0 mask 255.255.255.0
aggregate-address 10.10.0.0 255.255.0.0 summary-only
neighbor DMVPN-SPOKES peer-group
neighbor DMVPN-SPOKES remote-as 65001
neighbor DMVPN-SPOKES route-reflector-client
!
ip route 0.0.0.0 0.0.0.0 1.1.14.4
------------
R2 - Spoke:
------------
hostname R2
!
ip cef
!
crypto isakmp policy 10
encr aes
authentication pre-share
group 2
crypto isakmp key DmVpNpR3$h@r3dK3Y address 0.0.0.0
!
crypto ipsec transform-set TRANSFORM-SET esp-aes esp-sha-hmac
mode transport
!
crypto ipsec profile PROTECT-GRE
set transform-set TRANSFORM-SET
!
interface Tunnel0
bandwidth 4096
ip address 192.168.1.2 255.255.255.0
no ip redirects
ip mtu 1400
ip nhrp authentication NhRp@UtH
ip nhrp map multicast 1.1.14.1
ip nhrp map 192.168.1.1 1.1.14.1
ip nhrp network-id 100
ip nhrp nhs 192.168.1.1
ip nhrp shortcut
ip tcp adjust-mss 1360
tunnel source FastEthernet0/0
tunnel mode gre multipoint
tunnel key 123
tunnel protection ipsec profile PROTECT-GRE
!
interface FastEthernet0/0
ip address 1.1.24.2 255.255.255.0
!
interface FastEthernet0/1
ip address 10.10.2.2 255.255.255.0
!
router bgp 65001
bgp router-id 192.168.1.2
bgp log-neighbor-changes
network 10.10.2.0 mask 255.255.255.0
neighbor 192.168.1.1 remote-as 65001
!
ip route 0.0.0.0 0.0.0.0 1.1.24.4
------------
R3 - Spoke:
------------
hostname R3
!
ip cef
!
crypto isakmp policy 10
encr aes
authentication pre-share
group 2
crypto isakmp key DmVpNpR3$h@r3dK3Y address 0.0.0.0
!
crypto ipsec transform-set TRANSFORM-SET esp-aes esp-sha-hmac
mode transport
!
crypto ipsec profile PROTECT-GRE
set transform-set TRANSFORM-SET
!
interface Tunnel0
bandwidth 4096
ip address 192.168.1.3 255.255.255.0
no ip redirects
ip mtu 1400
ip nhrp authentication NhRp@UtH
ip nhrp map multicast 1.1.14.1
ip nhrp map 192.168.1.1 1.1.14.1
ip nhrp network-id 100
ip nhrp nhs 192.168.1.1
ip nhrp shortcut
ip tcp adjust-mss 1360
tunnel source FastEthernet0/0
tunnel mode gre multipoint
tunnel key 123
tunnel protection ipsec profile PROTECT-GRE
!
interface FastEthernet0/0
ip address 1.1.34.3 255.255.255.0
!
interface FastEthernet0/1
ip address 10.10.3.3 255.255.255.0
!
router bgp 65001
bgp router-id 192.168.1.3
bgp log-neighbor-changes
network 10.10.3.0 mask 255.255.255.0
neighbor 192.168.1.1 remote-as 65001
!
ip route 0.0.0.0 0.0.0.0 1.1.34.4
Verification:
- BGP peering between Hub and Spokes only, No spoke to spoke peering
R1#show ip bgp summary
BGP router identifier 192.168.1.1, local AS number 65001
BGP table version is 8, main routing table version 8
4 network entries using 592 bytes of memory
4 path entries using 256 bytes of memory
3/3 BGP path/bestpath attribute entries using 408 bytes of memory
0 BGP route-map cache entries using 0 bytes of memory
0 BGP filter-list cache entries using 0 bytes of memory
BGP using 1256 total bytes of memory
BGP activity 4/0 prefixes, 4/0 paths, scan interval 60 secs
Neighbor V AS MsgRcvd MsgSent TblVer InQ OutQ Up/Down State/PfxRcd
*192.168.1.2 4 65001 18 20 8 0 0 00:12:43 1
*192.168.1.3 4 65001 19 18 8 0 0 00:12:45 1
* Dynamically created based on a listen range command
Dynamically created neighbors: 2, Subnet ranges: 1
BGP peergroup DMVPN-SPOKES listen range group members:
192.168.1.0/24
Total dynamically created neighbors: 2/(50 max), Subnet ranges: 1
R2#show ip bgp summary
BGP router identifier 192.168.1.2, local AS number 65001
BGP table version is 3, main routing table version 3
2 network entries using 296 bytes of memory
2 path entries using 128 bytes of memory
2/2 BGP path/bestpath attribute entries using 272 bytes of memory
0 BGP route-map cache entries using 0 bytes of memory
0 BGP filter-list cache entries using 0 bytes of memory
BGP using 696 total bytes of memory
BGP activity 2/0 prefixes, 2/0 paths, scan interval 60 secs
Neighbor V AS MsgRcvd MsgSent TblVer InQ OutQ Up/Down State/PfxRcd
192.168.1.1 4 65001 20 18 3 0 0 00:12:50 1
R3#show ip bgp summary
BGP router identifier 192.168.1.3, local AS number 65001
BGP table version is 3, main routing table version 3
2 network entries using 296 bytes of memory
2 path entries using 128 bytes of memory
2/2 BGP path/bestpath attribute entries using 272 bytes of memory
0 BGP route-map cache entries using 0 bytes of memory
0 BGP filter-list cache entries using 0 bytes of memory
BGP using 696 total bytes of memory
BGP activity 2/0 prefixes, 2/0 paths, scan interval 60 secs
Neighbor V AS MsgRcvd MsgSent TblVer InQ OutQ Up/Down State/PfxRcd
192.168.1.1 4 65001 19 19 3 0 0 00:12:54 1
- Traffic between Spoke-R2 and Spoke-R3
R2#ping 10.10.3.3 so 10.10.2.2
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.10.3.3, timeout is 2 seconds:
Packet sent with a source address of 10.10.2.2
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 124/132/140 ms
R2#trace 10.10.3.3 so 10.10.2.2
Type escape sequence to abort.
Tracing the route to 10.10.3.3
VRF info: (vrf in name/id, vrf out name/id)
1 192.168.1.3 144 msec * 124 msec << Spoke R3 Tunnel IP
- DMVPN Status
R1#show dmvpn
Legend: Attrb --> S - Static, D - Dynamic, I - Incomplete
N - NATed, L - Local, X - No Socket
# Ent --> Number of NHRP entries with same NBMA peer
NHS Status: E --> Expecting Replies, R --> Responding, W --> Waiting
UpDn Time --> Up or Down Time for a Tunnel
======================================================================
Interface: Tunnel0, IPv4 NHRP Details
Type:Hub, NHRP Peers:2,
# Ent Peer NBMA Addr Peer Tunnel Add State UpDn Tm Attrb
----- --------------- --------------- ----- -------- -----
1 1.1.24.2 192.168.1.2 UP 00:15:42 D
1 1.1.34.3 192.168.1.3 UP 00:15:42 D
R2#show dmvpn
Legend: Attrb --> S - Static, D - Dynamic, I - Incomplete
N - NATed, L - Local, X - No Socket
# Ent --> Number of NHRP entries with same NBMA peer
NHS Status: E --> Expecting Replies, R --> Responding, W --> Waiting
UpDn Time --> Up or Down Time for a Tunnel
======================================================================
Interface: Tunnel0, IPv4 NHRP Details
Type:Spoke, NHRP Peers:2,
# Ent Peer NBMA Addr Peer Tunnel Add State UpDn Tm Attrb
----- --------------- --------------- ----- -------- -----
2 1.1.34.3 192.168.1.3 UP 00:01:20 DT1
192.168.1.3 UP 00:01:20 D
1 1.1.14.1 192.168.1.1 UP 00:15:47 S
*T1 - Route Installed
R3#show dmvpn
Legend: Attrb --> S - Static, D - Dynamic, I - Incomplete
N - NATed, L - Local, X - No Socket
# Ent --> Number of NHRP entries with same NBMA peer
NHS Status: E --> Expecting Replies, R --> Responding, W --> Waiting
UpDn Time --> Up or Down Time for a Tunnel
======================================================================
Interface: Tunnel0, IPv4 NHRP Details
Type:Spoke, NHRP Peers:2,
# Ent Peer NBMA Addr Peer Tunnel Add State UpDn Tm Attrb
----- --------------- --------------- ----- -------- -----
2 1.1.24.2 192.168.1.2 UP 00:01:23 DT1
192.168.1.2 UP 00:01:23 D
1 1.1.14.1 192.168.1.1 UP 00:15:49 S
*T1 - Route Installed
- BGP Table
R1#show ip bgp
BGP table version is 8, local router ID is 192.168.1.1
Status codes: s suppressed, d damped, h history, * valid, > best, i - internal,
r RIB-failure, S Stale, m multipath, b backup-path, f RT-Filter,
x best-external, a additional-path, c RIB-compressed,
Origin codes: i - IGP, e - EGP, ? - incomplete
RPKI validation codes: V valid, I invalid, N Not found
Network Next Hop Metric LocPrf Weight Path
*> 10.10.0.0/16 0.0.0.0 32768 i
s> 10.10.1.0/24 0.0.0.0 0 32768 i
s>i 10.10.2.0/24 192.168.1.2 0 100 0 i
s>i 10.10.3.0/24 192.168.1.3 0 100 0 i
R2#show ip bgp
BGP table version is 3, local router ID is 192.168.1.2
Status codes: s suppressed, d damped, h history, * valid, > best, i - internal,
r RIB-failure, S Stale, m multipath, b backup-path, f RT-Filter,
x best-external, a additional-path, c RIB-compressed,
Origin codes: i - IGP, e - EGP, ? - incomplete
RPKI validation codes: V valid, I invalid, N Not found
Network Next Hop Metric LocPrf Weight Path
*>i 10.10.0.0/16 192.168.1.1 0 100 0 i
*> 10.10.2.0/24 0.0.0.0 0 32768 i
R3#show ip bgp
BGP table version is 3, local router ID is 192.168.1.3
Status codes: s suppressed, d damped, h history, * valid, > best, i - internal,
r RIB-failure, S Stale, m multipath, b backup-path, f RT-Filter,
x best-external, a additional-path, c RIB-compressed,
Origin codes: i - IGP, e - EGP, ? - incomplete
RPKI validation codes: V valid, I invalid, N Not found
Network Next Hop Metric LocPrf Weight Path
*>i 10.10.0.0/16 192.168.1.1 0 100 0 i
*> 10.10.3.0/24 0.0.0.0 0 32768 i
- Routing Table
R1#show ip route
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
o - ODR, P - periodic downloaded static route, H - NHRP, l - LISP
+ - replicated route, % - next hop override
Gateway of last resort is 1.1.14.4 to network 0.0.0.0
S* 0.0.0.0/0 [1/0] via 1.1.14.4
1.0.0.0/8 is variably subnetted, 2 subnets, 2 masks
C 1.1.14.0/24 is directly connected, FastEthernet0/0
L 1.1.14.1/32 is directly connected, FastEthernet0/0
10.0.0.0/8 is variably subnetted, 5 subnets, 3 masks
B 10.10.0.0/16 [200/0] via 0.0.0.0, 00:17:13, Null0
C 10.10.1.0/24 is directly connected, FastEthernet0/1
L 10.10.1.1/32 is directly connected, FastEthernet0/1
B 10.10.2.0/24 [200/0] via 192.168.1.2, 00:16:05
B 10.10.3.0/24 [200/0] via 192.168.1.3, 00:16:57
192.168.1.0/24 is variably subnetted, 2 subnets, 2 masks
C 192.168.1.0/24 is directly connected, Tunnel0
L 192.168.1.1/32 is directly connected, Tunnel0
R2#show ip route
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
o - ODR, P - periodic downloaded static route, H - NHRP, l - LISP
+ - replicated route, % - next hop override
Gateway of last resort is 1.1.24.4 to network 0.0.0.0
S* 0.0.0.0/0 [1/0] via 1.1.24.4
1.0.0.0/8 is variably subnetted, 2 subnets, 2 masks
C 1.1.24.0/24 is directly connected, FastEthernet0/0
L 1.1.24.2/32 is directly connected, FastEthernet0/0
10.0.0.0/8 is variably subnetted, 4 subnets, 3 masks
B 10.10.0.0/16 [200/0] via 192.168.1.1, 00:16:11
C 10.10.2.0/24 is directly connected, FastEthernet0/1
L 10.10.2.2/32 is directly connected, FastEthernet0/1
H 10.10.3.0/24 [250/1] via 192.168.1.3, 00:02:52, Tunnel0
192.168.1.0/24 is variably subnetted, 2 subnets, 2 masks
C 192.168.1.0/24 is directly connected, Tunnel0
L 192.168.1.2/32 is directly connected, Tunnel0
R3#show ip route
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
o - ODR, P - periodic downloaded static route, H - NHRP, l - LISP
+ - replicated route, % - next hop override
Gateway of last resort is 1.1.34.4 to network 0.0.0.0
S* 0.0.0.0/0 [1/0] via 1.1.34.4
1.0.0.0/8 is variably subnetted, 2 subnets, 2 masks
C 1.1.34.0/24 is directly connected, FastEthernet0/0
L 1.1.34.3/32 is directly connected, FastEthernet0/0
10.0.0.0/8 is variably subnetted, 4 subnets, 3 masks
B 10.10.0.0/16 [200/0] via 192.168.1.1, 00:17:06
H 10.10.2.0/24 [250/1] via 192.168.1.2, 00:02:55, Tunnel0
C 10.10.3.0/24 is directly connected, FastEthernet0/1
L 10.10.3.3/32 is directly connected, FastEthernet0/1
192.168.1.0/24 is variably subnetted, 2 subnets, 2 masks
C 192.168.1.0/24 is directly connected, Tunnel0
L 192.168.1.3/32 is directly connected, Tunnel0
- NHRP Table
R1#show ip nhrp
192.168.1.2/32 via 192.168.1.2
Tunnel0 created 00:17:49, expire 01:42:10
Type: dynamic, Flags: unique registered used
NBMA address: 1.1.24.2
192.168.1.3/32 via 192.168.1.3
Tunnel0 created 00:17:49, expire 01:42:11
Type: dynamic, Flags: unique registered used
NBMA address: 1.1.34.3
R2#show ip nhrp
10.10.2.0/24 via 192.168.1.2
Tunnel0 created 00:03:27, expire 01:56:32
Type: dynamic, Flags: router unique local
NBMA address: 1.1.24.2
(no-socket)
10.10.3.0/24 via 192.168.1.3
Tunnel0 created 00:03:27, expire 01:56:31
Type: dynamic, Flags: router used rib
NBMA address: 1.1.34.3
192.168.1.1/32 via 192.168.1.1
Tunnel0 created 00:18:28, never expire
Type: static, Flags: used
NBMA address: 1.1.14.1
192.168.1.3/32 via 192.168.1.3
Tunnel0 created 00:03:28, expire 01:56:32
Type: dynamic, Flags: router implicit used
NBMA address: 1.1.34.3
R3#show ip nhrp
10.10.2.0/24 via 192.168.1.2
Tunnel0 created 00:03:29, expire 01:56:30
Type: dynamic, Flags: router used rib
NBMA address: 1.1.24.2
10.10.3.0/24 via 192.168.1.3
Tunnel0 created 00:03:30, expire 01:56:29
Type: dynamic, Flags: router unique local
NBMA address: 1.1.34.3
(no-socket)
192.168.1.1/32 via 192.168.1.1
Tunnel0 created 00:18:31, never expire
Type: static, Flags: used
NBMA address: 1.1.14.1
192.168.1.2/32 via 192.168.1.2
Tunnel0 created 00:03:31, expire 01:56:29
Type: dynamic, Flags: router implicit used
NBMA address: 1.1.24.2