Integrated IS-IS IPv6 Configuration
We will cover following topics:
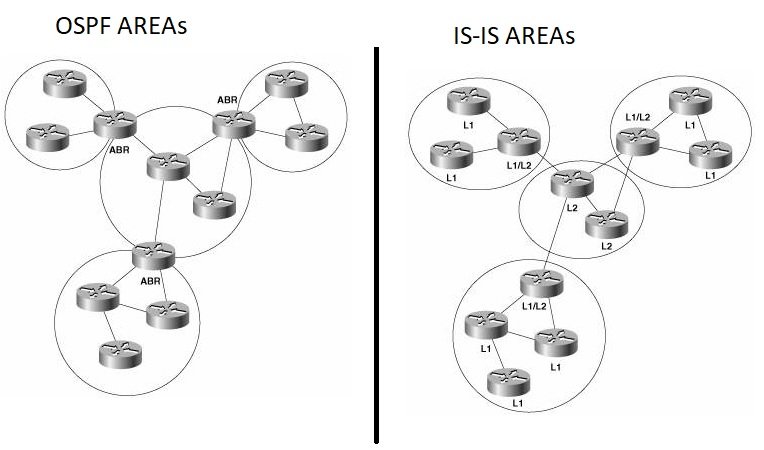
- Multiple IS-IS Areas
- IS-IS Metric Styles – Narrow and Wide
- IS-IS Single/Multi Topology
- Route Leak between Areas
- Route Summarization
- Redistribution between IS-IS and other routing protocol
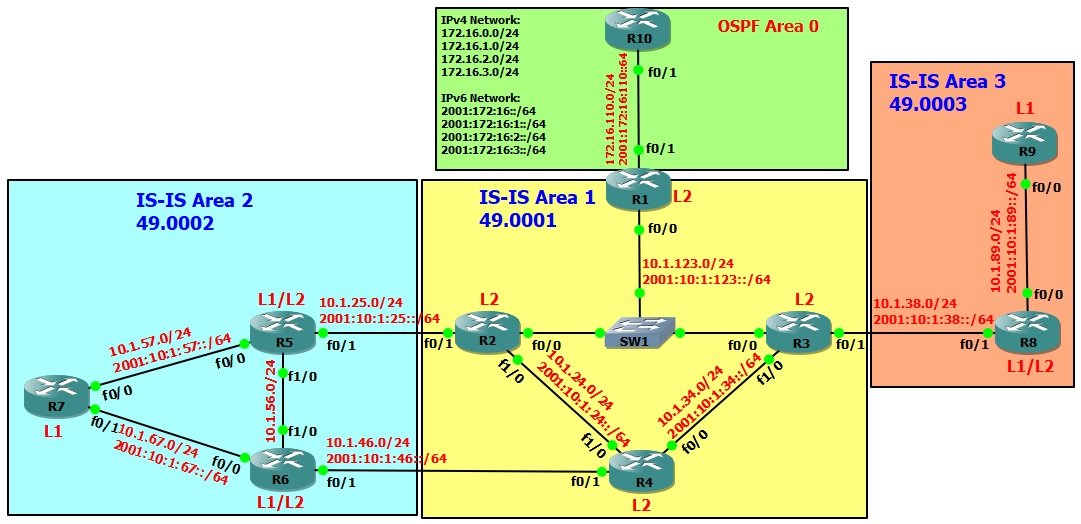
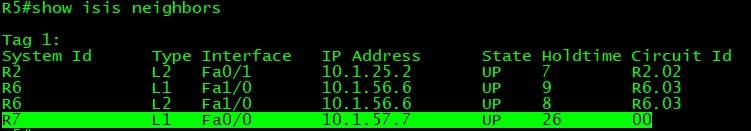
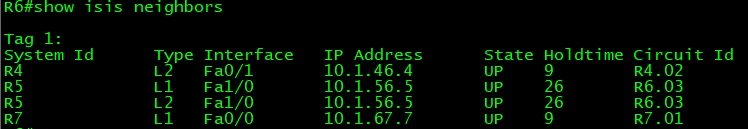
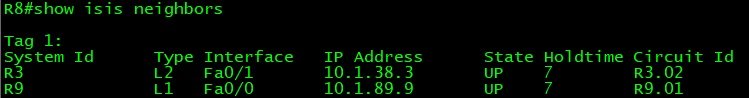
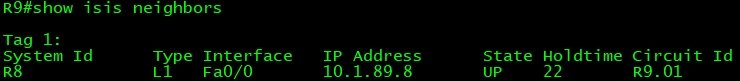
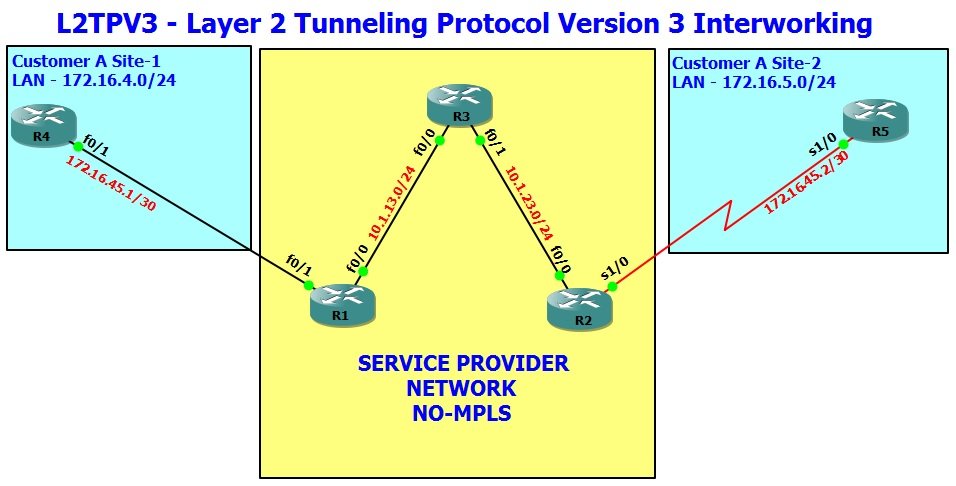
Network Topology
You can find Integrated IS-IS IPv4 configuration for same topology at http://www.amolak.net/integrated-is-is-ipv4-configuration/
Tasks
- Configure IS-IS Area 49.0001 on R1, R2, R3 & R4.
- Configure IS-IS Area 49.0002 on R5, R6 & R7.
- Configure IS-IS Area 49.0003 on R8 & R9.
- Configure OSPF Area 0 between R1 Fa0/1 and R10 Fa0/1.
- Configure R1, R2 & R3 as IS-IS Router type Level-2 only.
- Configure all interfaces of R4 as IS-IS circuit type Level-2 only.
- R5, R6 & R8 would work in default IS-IS router type, which is L1/L2.
- Configure R7 & R9 as IS-IS Router type Level-1.
- Configure mutual redistribution between OSPF and IS-IS on R1.
- Configure R8 to Leak Level-2 area routes into Level-1 area.
- Configure R8 to send summary route 2001:172:16::/48 instead of more specific routes from 2001:172:16:xx network, into Level-1 area.
Configuration
R1 hostname R1 ! ip cef ipv6 unicast-routing ipv6 cef ! interface Loopback0 ip address 192.168.1.1 255.255.255.255 ipv6 address 2001:192:168:1::1/128 ! interface FastEthernet0/0 ip address 10.1.123.1 255.255.255.0 ip router isis 1 ipv6 address 2001:10:1:123::1/64 ipv6 router isis 1 ! interface FastEthernet0/1 ip address 172.16.110.1 255.255.255.0 ipv6 address 2001:172:16:110::1/64 ipv6 ospf 100 area 0 ! router ospf 1 redistribute isis 1 level-1-2 subnets passive-interface default no passive-interface FastEthernet0/1 network 172.16.110.1 0.0.0.0 area 0 network 192.168.1.1 0.0.0.0 area 0 ! router isis 1 net 49.0001.1921.6800.1001.00 is-type level-2-only redistribute ospf 1 match internal external 1 external 2 passive-interface Loopback0 ! address-family ipv6 redistribute ospf 100 match internal external 1 external 2 exit-address-family ! ipv6 router ospf 100 redistribute isis 1 level-1-2 ! R2 hostname R2 ! ip cef ipv6 unicast-routing ipv6 cef ! interface Loopback0 ip address 192.168.1.2 255.255.255.255 ipv6 address 2001:192:168:1::2/128 ! interface FastEthernet0/0 ip address 10.1.123.2 255.255.255.0 ip router isis 1 ipv6 address 2001:10:1:123::2/64 ipv6 router isis 1 ! interface FastEthernet0/1 ip address 10.1.25.2 255.255.255.0 ip router isis 1 ipv6 address 2001:10:1:25::2/64 ipv6 router isis 1 ! interface FastEthernet1/0 ip address 10.1.24.2 255.255.255.0 ip router isis 1 ipv6 address 2001:10:1:24::2/64 ipv6 router isis 1 ! router isis 1 net 49.0001.1921.6800.1002.00 is-type level-2-only passive-interface Loopback0 ! R3 hostname R3 ! ip cef ipv6 unicast-routing ipv6 cef ! interface Loopback0 ip address 192.168.1.3 255.255.255.255 ipv6 address 2001:192:168:1::3/128 ! interface FastEthernet0/0 ip address 10.1.123.3 255.255.255.0 ip router isis 1 ipv6 address 2001:10:1:123::3/64 ipv6 router isis 1 ! interface FastEthernet0/1 ip address 10.1.38.3 255.255.255.0 ip router isis 1 ipv6 address 2001:10:1:38::3/64 ipv6 router isis 1 ! interface FastEthernet1/0 ip address 10.1.34.3 255.255.255.0 ip router isis 1 ipv6 address 2001:10:1:34::3/64 ipv6 router isis 1 ! router isis 1 net 49.0001.1921.6800.1003.00 is-type level-2-only passive-interface Loopback0 ! R4 hostname R4 ! ip cef ipv6 unicast-routing ipv6 cef ! interface Loopback0 ip address 192.168.1.4 255.255.255.255 ipv6 address 2001:192:168:1::4/128 ! interface FastEthernet0/0 ip address 10.1.34.4 255.255.255.0 ip router isis 1 ipv6 address 2001:10:1:34::4/64 ipv6 router isis 1 isis circuit-type level-2-only ! interface FastEthernet0/1 ip address 10.1.46.4 255.255.255.0 ip router isis 1 ipv6 address 2001:10:1:46::4/64 ipv6 router isis 1 isis circuit-type level-2-only ! interface FastEthernet1/0 ip address 10.1.24.4 255.255.255.0 ip router isis 1 ipv6 address 2001:10:1:24::4/64 ipv6 router isis 1 isis circuit-type level-2-only ! router isis 1 net 49.0001.1921.6800.1004.00 passive-interface Loopback0 ! R5 hostname R5 ! ip cef ipv6 unicast-routing ipv6 cef ! interface Loopback0 ip address 192.168.1.5 255.255.255.255 ipv6 address 2001:192:168:1::5/128 ! interface FastEthernet0/0 ip address 10.1.57.5 255.255.255.0 ip router isis 1 ipv6 address 2001:10:1:57::5/64 ipv6 router isis 1 isis network point-to-point ! interface FastEthernet0/1 ip address 10.1.25.5 255.255.255.0 ip router isis 1 ipv6 address 2001:10:1:25::5/64 ipv6 router isis 1 ! interface FastEthernet1/0 ip address 10.1.56.5 255.255.255.0 ip router isis 1 ipv6 address 2001:10:1:56::5/64 ipv6 router isis 1 ! router isis 1 net 49.0002.1921.6800.1005.00 passive-interface Loopback0 ! R6 hostname R6 ! ip cef ipv6 unicast-routing ipv6 cef ! interface Loopback0 ip address 192.168.1.6 255.255.255.255 ipv6 address 2001:192:168:1::6/128 ! interface FastEthernet0/0 ip address 10.1.67.6 255.255.255.0 ip router isis 1 ipv6 address 2001:10:1:67::6/64 ipv6 router isis 1 ! interface FastEthernet0/1 ip address 10.1.46.6 255.255.255.0 ip router isis 1 ipv6 address 2001:10:1:46::6/64 ipv6 router isis 1 ! interface FastEthernet1/0 ip address 10.1.56.6 255.255.255.0 ip router isis 1 ipv6 address 2001:10:1:56::6/64 ipv6 router isis 1 ! router isis 1 net 49.0002.1921.6800.1006.00 passive-interface Loopback0 ! R7 hostname R7 ! ip cef ipv6 unicast-routing ipv6 cef ! interface Loopback0 ip address 192.168.1.7 255.255.255.255 ipv6 address 2001:192:168:1::7/128 ! interface FastEthernet0/0 ip address 10.1.57.7 255.255.255.0 ip router isis 1 ipv6 address 2001:10:1:57::7/64 ipv6 router isis 1 isis network point-to-point isis ipv6 metric 20 ! interface FastEthernet0/1 ip address 10.1.67.7 255.255.255.0 ip router isis 1 ipv6 address 2001:10:1:67::7/64 ipv6 router isis 1 isis metric 20 ! router isis 1 net 49.0002.1921.6800.1007.00 is-type level-1 passive-interface Loopback0 ! R8 hostname R8 ! ip cef ipv6 unicast-routing ipv6 cef ! interface Loopback0 ip address 192.168.1.8 255.255.255.255 ipv6 address 2001:192:168:1::8/128 ! interface FastEthernet0/0 ip address 10.1.89.8 255.255.255.0 ip router isis 1 ipv6 address 2001:10:1:89::8/64 ipv6 router isis 1 ! interface FastEthernet0/1 ip address 10.1.38.8 255.255.255.0 ip router isis 1 ipv6 address 2001:10:1:38::8/64 ipv6 router isis 1 ! router isis 1 net 49.0003.1921.6800.1008.00 summary-address 172.16.0.0 255.255.252.0 level-1 redistribute isis ip level-2 into level-1 distribute-list 100 passive-interface Loopback0 ! address-family ipv6 summary-prefix 2001:172:16::/48 level-1 redistribute isis level-2 into level-1 distribute-list IPv6_L2_PREFIXES exit-address-family ! access-list 100 permit ip any any ! ipv6 prefix-list IPv6_L2_PREFIXES seq 5 permit ::/0 le 128 ! R9 hostname R9 ! ip cef ipv6 unicast-routing ipv6 cef ! interface Loopback0 ip address 192.168.1.9 255.255.255.255 ipv6 address 2001:192:168:1::9/128 ! interface FastEthernet0/0 ip address 10.1.89.9 255.255.255.0 ip router isis 1 ipv6 address 2001:10:1:89::9/64 ipv6 router isis 1 ! router isis 1 net 49.0003.1921.6800.1009.00 is-type level-1 passive-interface Loopback0 ! R10 hostname R10 ! ip cef ipv6 unicast-routing ipv6 cef ! interface Loopback0 ip address 192.168.1.10 255.255.255.255 ipv6 address 2001:192:168:1::10/128 ipv6 ospf 100 area 0 ! interface Loopback1 ip address 172.16.0.1 255.255.255.0 ip ospf network point-to-point ipv6 address 2001:172:16::1/64 ipv6 ospf 100 area 0 ipv6 ospf network point-to-point ! interface Loopback2 ip address 172.16.1.1 255.255.255.0 ip ospf network point-to-point ipv6 address 2001:172:16:1::1/64 ipv6 ospf 100 area 0 ipv6 ospf network point-to-point ! interface Loopback3 ip address 172.16.2.1 255.255.255.0 ip ospf network point-to-point ipv6 address 2001:172:16:2::1/64 ipv6 ospf 100 area 0 ipv6 ospf network point-to-point ! interface Loopback4 ip address 172.16.3.1 255.255.255.0 ip ospf network point-to-point ipv6 address 2001:172:16:3::1/64 ipv6 ospf 100 area 0 ipv6 ospf network point-to-point ! interface FastEthernet0/1 ip address 172.16.110.10 255.255.255.0 ipv6 address 2001:172:16:110::10/64 ipv6 ospf 100 area 0 ! router ospf 1 network 0.0.0.0 255.255.255.255 area 0 ! ipv6 router ospf 100 !
Task Specific Configuration Explanation
Task 1 – 3
To enable Integrated IS-IS routing for IPv6, first we need to enable “ipv6 unicast-routing” in global configuration and then configure “ipv6 router isis x” under interfaces, which are configured for IPv6 networks.
Task 4
Configure OSPFv3 for IPv6:
- Configure OSPFv3 process ID for IPv6 – ipv6 router ospf 100
- Configure IPv6 OSPF process id and area under interfaces – ipv6 ospf 100 area 0
Task 9
OSPF to IS-IS Redistribution
We need to define which OSPF routes need to be redistributed into IS-IS in address-family IPv6. Here we have matched all OSPF route types – internal, external type 1 (E1), external type 2 (E2)
router isis 1 ! address-family ipv6 redistribute ospf 100 match internal external 1 external 2 exit-address-family
IS-IS to OSPF Redistribution
We need to define which IS-IS routes need to be redistributed into OSPF. Here we have matched both level1 and level2 routes with their actual subnet mask.
ipv6 router ospf 100 redistribute isis 1 level-1-2
Task 10 – Route Leak
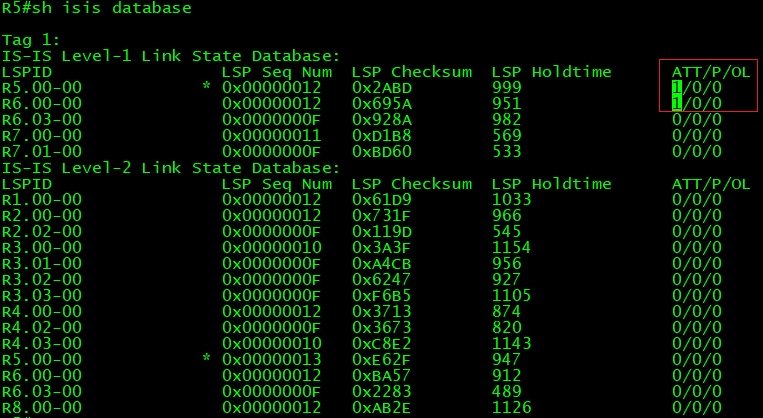
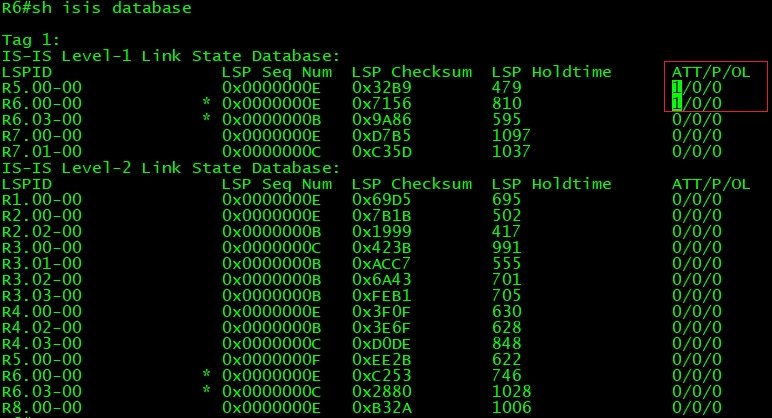
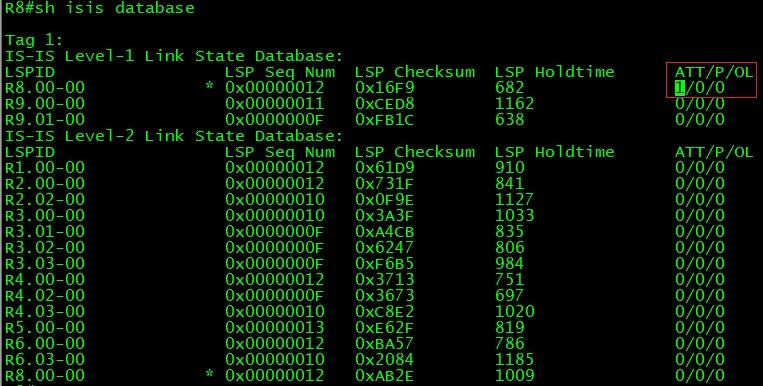
IS-IS level1 area is like OSPF totally stubby area, which receives default route from Area Border Router to reach all destinations outside of its own area. Let’s check routing table on R9 (Level-1 Router) before leaking level2 routes into level1 area.
R9#sh ipv6 route IPv6 Routing Table - default - 7 entries Codes: C - Connected, L - Local, S - Static, U - Per-user Static route B - BGP, HA - Home Agent, MR - Mobile Router, R - RIP H - NHRP, I1 - ISIS L1, I2 - ISIS L2, IA - ISIS interarea IS - ISIS summary, D - EIGRP, EX - EIGRP external, NM - NEMO ND - ND Default, NDp - ND Prefix, DCE - Destination, NDr - Redirect O - OSPF Intra, OI - OSPF Inter, OE1 - OSPF ext 1, OE2 - OSPF ext 2 ON1 - OSPF NSSA ext 1, ON2 - OSPF NSSA ext 2, l - LISP I1 ::/0 [115/10] via FE80::C803:29FF:FE90:8, FastEthernet0/0 I1 2001:10:1:38::/64 [115/20] via FE80::C803:29FF:FE90:8, FastEthernet0/0 C 2001:10:1:89::/64 [0/0] via FastEthernet0/0, directly connected L 2001:10:1:89::9/128 [0/0] via FastEthernet0/0, receive I1 2001:192:168:1::8/128 [115/10] via FE80::C803:29FF:FE90:8, FastEthernet0/0 LC 2001:192:168:1::9/128 [0/0] via Loopback0, receive L FF00::/8 [0/0] via Null0, receive
Let’s configure route leak level2 routes into level1 on R8. We can create IPv6 prefix-list to match IPv6 routes, which we want to leak from level2 into level1.
R8#conf t
Enter configuration commands, one per line. End with CNTL/Z.
R8(config)#ipv6 prefix-list IPv6_L2_PREFIXES seq 5 permit ::/0 le 128
R8(config)#router isis 1
R8(config-router)#address-family ipv6
R8(config-router)#redistribute isis level-2 into level-1 distribute-list IPv6_L2_PREFIXES
R8(config-router)#end
R8#
Now check routing on R9(Level1 Router)
R9#sh ipv6 route IPv6 Routing Table - default - 27 entries Codes: C - Connected, L - Local, S - Static, U - Per-user Static route B - BGP, HA - Home Agent, MR - Mobile Router, R - RIP H - NHRP, I1 - ISIS L1, I2 - ISIS L2, IA - ISIS interarea IS - ISIS summary, D - EIGRP, EX - EIGRP external, NM - NEMO ND - ND Default, NDp - ND Prefix, DCE - Destination, NDr - Redirect O - OSPF Intra, OI - OSPF Inter, OE1 - OSPF ext 1, OE2 - OSPF ext 2 ON1 - OSPF NSSA ext 1, ON2 - OSPF NSSA ext 2, l - LISP I1 ::/0 [115/10] via FE80::C803:29FF:FE90:8, FastEthernet0/0 IA 2001:10:1:24::/64 [115/40] via FE80::C803:29FF:FE90:8, FastEthernet0/0 IA 2001:10:1:25::/64 [115/40] via FE80::C803:29FF:FE90:8, FastEthernet0/0 IA 2001:10:1:34::/64 [115/30] via FE80::C803:29FF:FE90:8, FastEthernet0/0 I1 2001:10:1:38::/64 [115/20] via FE80::C803:29FF:FE90:8, FastEthernet0/0 IA 2001:10:1:46::/64 [115/40] via FE80::C803:29FF:FE90:8, FastEthernet0/0 IA 2001:10:1:56::/64 [115/50] via FE80::C803:29FF:FE90:8, FastEthernet0/0 IA 2001:10:1:57::/64 [115/50] via FE80::C803:29FF:FE90:8, FastEthernet0/0 IA 2001:10:1:67::/64 [115/50] via FE80::C803:29FF:FE90:8, FastEthernet0/0 C 2001:10:1:89::/64 [0/0] via FastEthernet0/0, directly connected L 2001:10:1:89::9/128 [0/0] via FastEthernet0/0, receive IA 2001:10:1:123::/64 [115/30] via FE80::C803:29FF:FE90:8, FastEthernet0/0 IA 2001:172:16::/64 [115/30] via FE80::C803:29FF:FE90:8, FastEthernet0/0 IA 2001:172:16:1::/64 [115/30] via FE80::C803:29FF:FE90:8, FastEthernet0/0 IA 2001:172:16:2::/64 [115/30] via FE80::C803:29FF:FE90:8, FastEthernet0/0 IA 2001:172:16:3::/64 [115/30] via FE80::C803:29FF:FE90:8, FastEthernet0/0 IA 2001:192:168:1::1/128 [115/30] via FE80::C803:29FF:FE90:8, FastEthernet0/0 IA 2001:192:168:1::2/128 [115/30] via FE80::C803:29FF:FE90:8, FastEthernet0/0 IA 2001:192:168:1::3/128 [115/20] via FE80::C803:29FF:FE90:8, FastEthernet0/0 IA 2001:192:168:1::4/128 [115/30] via FE80::C803:29FF:FE90:8, FastEthernet0/0 IA 2001:192:168:1::5/128 [115/40] via FE80::C803:29FF:FE90:8, FastEthernet0/0 IA 2001:192:168:1::6/128 [115/40] via FE80::C803:29FF:FE90:8, FastEthernet0/0 IA 2001:192:168:1::7/128 [115/50] via FE80::C803:29FF:FE90:8, FastEthernet0/0 I1 2001:192:168:1::8/128 [115/10] via FE80::C803:29FF:FE90:8, FastEthernet0/0 LC 2001:192:168:1::9/128 [0/0] via Loopback0, receive IA 2001:192:168:1::10/128 [115/30] via FE80::C803:29FF:FE90:8, FastEthernet0/0 L FF00::/8 [0/0] via Null0, receive R9#
Task 11 – Route Summarization
As we have seen in previous routing table on R9, it has received below four routes from R8.
2001:172:16::/64
2001:172:16:1::/64
2001:172:16:2::/64
2001:172:16:3::/64
which can be summarized into 2001:172:16::/48.
R8#conf t Enter configuration commands, one per line. End with CNTL/Z. R8(config)#router isis 1 R8(config-router)#address-family ipv6 R8(config-router-af)#summary-prefix 2001:172:16::/48 level-1 R8(config-router-af)# R8(config-router-af)#end R8# !! -- When doing manual summarization the router will add a local --!! !!-- summary route to null 0. This feature is in place to prevent --!! !! -- routing loops. --!! R8#sh ipv6 route IPv6 Routing Table - default - 28 entries Codes: C - Connected, L - Local, S - Static, U - Per-user Static route B - BGP, HA - Home Agent, MR - Mobile Router, R - RIP H - NHRP, I1 - ISIS L1, I2 - ISIS L2, IA - ISIS interarea IS - ISIS summary, D - EIGRP, EX - EIGRP external, NM - NEMO ND - ND Default, NDp - ND Prefix, DCE - Destination, NDr - Redirect O - OSPF Intra, OI - OSPF Inter, OE1 - OSPF ext 1, OE2 - OSPF ext 2 ON1 - OSPF NSSA ext 1, ON2 - OSPF NSSA ext 2, l - LISP I2 2001:10:1:24::/64 [115/30] via FE80::C807:1EFF:FE84:6, FastEthernet0/1 I2 2001:10:1:25::/64 [115/30] via FE80::C807:1EFF:FE84:6, FastEthernet0/1 I2 2001:10:1:34::/64 [115/20] via FE80::C807:1EFF:FE84:6, FastEthernet0/1 C 2001:10:1:38::/64 [0/0] via FastEthernet0/1, directly connected L 2001:10:1:38::8/128 [0/0] via FastEthernet0/1, receive I2 2001:10:1:46::/64 [115/30] via FE80::C807:1EFF:FE84:6, FastEthernet0/1 I2 2001:10:1:56::/64 [115/40] via FE80::C807:1EFF:FE84:6, FastEthernet0/1 I2 2001:10:1:57::/64 [115/40] via FE80::C807:1EFF:FE84:6, FastEthernet0/1 I2 2001:10:1:67::/64 [115/40] via FE80::C807:1EFF:FE84:6, FastEthernet0/1 C 2001:10:1:89::/64 [0/0] via FastEthernet0/0, directly connected L 2001:10:1:89::8/128 [0/0] via FastEthernet0/0, receive I2 2001:10:1:123::/64 [115/20] via FE80::C807:1EFF:FE84:6, FastEthernet0/1 IS 2001:172:16::/48 [115/20] via Null0, directly connected I2 2001:172:16::/64 [115/20] via FE80::C807:1EFF:FE84:6, FastEthernet0/1 I2 2001:172:16:1::/64 [115/20] via FE80::C807:1EFF:FE84:6, FastEthernet0/1 I2 2001:172:16:2::/64 [115/20] via FE80::C807:1EFF:FE84:6, FastEthernet0/1 I2 2001:172:16:3::/64 [115/20] via FE80::C807:1EFF:FE84:6, FastEthernet0/1 I2 2001:192:168:1::1/128 [115/20] via FE80::C807:1EFF:FE84:6, FastEthernet0/1 I2 2001:192:168:1::2/128 [115/20] via FE80::C807:1EFF:FE84:6, FastEthernet0/1 I2 2001:192:168:1::3/128 [115/10] via FE80::C807:1EFF:FE84:6, FastEthernet0/1 I2 2001:192:168:1::4/128 [115/20] via FE80::C807:1EFF:FE84:6, FastEthernet0/1 I2 2001:192:168:1::5/128 [115/30] via FE80::C807:1EFF:FE84:6, FastEthernet0/1 I2 2001:192:168:1::6/128 [115/30] via FE80::C807:1EFF:FE84:6, FastEthernet0/1 I2 2001:192:168:1::7/128 [115/40] via FE80::C807:1EFF:FE84:6, FastEthernet0/1 LC 2001:192:168:1::8/128 [0/0] via Loopback0, receive I1 2001:192:168:1::9/128 [115/10] via FE80::C808:33FF:FE70:8, FastEthernet0/0 I2 2001:192:168:1::10/128 [115/20] via FE80::C807:1EFF:FE84:6, FastEthernet0/1 L FF00::/8 [0/0] via Null0, receive R8# !! -- Now check routing table on R9. -- !! R9#sh ipv6 route IPv6 Routing Table - default - 24 entries Codes: C - Connected, L - Local, S - Static, U - Per-user Static route B - BGP, HA - Home Agent, MR - Mobile Router, R - RIP H - NHRP, I1 - ISIS L1, I2 - ISIS L2, IA - ISIS interarea IS - ISIS summary, D - EIGRP, EX - EIGRP external, NM - NEMO ND - ND Default, NDp - ND Prefix, DCE - Destination, NDr - Redirect O - OSPF Intra, OI - OSPF Inter, OE1 - OSPF ext 1, OE2 - OSPF ext 2 ON1 - OSPF NSSA ext 1, ON2 - OSPF NSSA ext 2, l - LISP I1 ::/0 [115/10] via FE80::C803:29FF:FE90:8, FastEthernet0/0 IA 2001:10:1:24::/64 [115/40] via FE80::C803:29FF:FE90:8, FastEthernet0/0 IA 2001:10:1:25::/64 [115/40] via FE80::C803:29FF:FE90:8, FastEthernet0/0 IA 2001:10:1:34::/64 [115/30] via FE80::C803:29FF:FE90:8, FastEthernet0/0 I1 2001:10:1:38::/64 [115/20] via FE80::C803:29FF:FE90:8, FastEthernet0/0 IA 2001:10:1:46::/64 [115/40] via FE80::C803:29FF:FE90:8, FastEthernet0/0 IA 2001:10:1:56::/64 [115/50] via FE80::C803:29FF:FE90:8, FastEthernet0/0 IA 2001:10:1:57::/64 [115/50] via FE80::C803:29FF:FE90:8, FastEthernet0/0 IA 2001:10:1:67::/64 [115/50] via FE80::C803:29FF:FE90:8, FastEthernet0/0 C 2001:10:1:89::/64 [0/0] via FastEthernet0/0, directly connected L 2001:10:1:89::9/128 [0/0] via FastEthernet0/0, receive IA 2001:10:1:123::/64 [115/30] via FE80::C803:29FF:FE90:8, FastEthernet0/0 IA 2001:172:16::/48 [115/30] via FE80::C803:29FF:FE90:8, FastEthernet0/0 IA 2001:192:168:1::1/128 [115/30] via FE80::C803:29FF:FE90:8, FastEthernet0/0 IA 2001:192:168:1::2/128 [115/30] via FE80::C803:29FF:FE90:8, FastEthernet0/0 IA 2001:192:168:1::3/128 [115/20] via FE80::C803:29FF:FE90:8, FastEthernet0/0 IA 2001:192:168:1::4/128 [115/30] via FE80::C803:29FF:FE90:8, FastEthernet0/0 IA 2001:192:168:1::5/128 [115/40] via FE80::C803:29FF:FE90:8, FastEthernet0/0 IA 2001:192:168:1::6/128 [115/40] via FE80::C803:29FF:FE90:8, FastEthernet0/0 IA 2001:192:168:1::7/128 [115/50] via FE80::C803:29FF:FE90:8, FastEthernet0/0 I1 2001:192:168:1::8/128 [115/10] via FE80::C803:29FF:FE90:8, FastEthernet0/0 LC 2001:192:168:1::9/128 [0/0] via Loopback0, receive IA 2001:192:168:1::10/128 [115/30] via FE80::C803:29FF:FE90:8, FastEthernet0/0 L FF00::/8 [0/0] via Null0, receive R9#
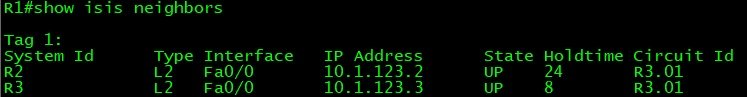
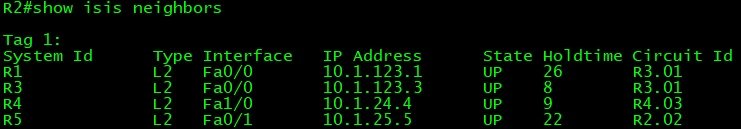
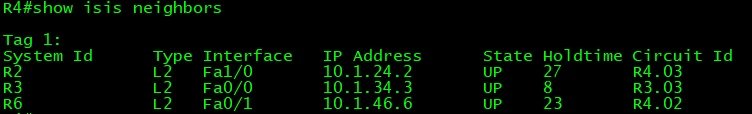
Verification and Testing
!! -- "show clns protocol" output shows that all interfaces are -- !! !! -- running both IP (IPv4) and IPv6 address family. --!! R1#show clns protocol IS-IS Router: 1 System Id: 1921.6800.1001.00 IS-Type: level-2 Manual area address(es): 49.0001 Routing for area address(es): 49.0001 Interfaces supported by IS-IS: FastEthernet0/0 - IP - IPv6 Passive interface: Loopback0 Redistribute: static (on by default) Distance for L2 CLNS routes: 110 RRR level: none Generate narrow metrics: level-1-2 Accept narrow metrics: level-1-2 Generate wide metrics: none Accept wide metrics: none R2#show clns protocol IS-IS Router: 1 System Id: 1921.6800.1002.00 IS-Type: level-2 Manual area address(es): 49.0001 Routing for area address(es): 49.0001 Interfaces supported by IS-IS: FastEthernet1/0 - IP - IPv6 FastEthernet0/1 - IP - IPv6 FastEthernet0/0 - IP - IPv6 Passive interface: Loopback0 Redistribute: static (on by default) Distance for L2 CLNS routes: 110 RRR level: none Generate narrow metrics: level-1-2 Accept narrow metrics: level-1-2 Generate wide metrics: none Accept wide metrics: none R3#show clns protocol IS-IS Router: 1 System Id: 1921.6800.1003.00 IS-Type: level-2 Manual area address(es): 49.0001 Routing for area address(es): 49.0001 Interfaces supported by IS-IS: FastEthernet1/0 - IP - IPv6 FastEthernet0/1 - IP - IPv6 FastEthernet0/0 - IP - IPv6 Passive interface: Loopback0 Redistribute: static (on by default) Distance for L2 CLNS routes: 110 RRR level: none Generate narrow metrics: level-1-2 Accept narrow metrics: level-1-2 Generate wide metrics: none Accept wide metrics: none R4#show clns protocol IS-IS Router: 1 System Id: 1921.6800.1004.00 IS-Type: level-1-2 Manual area address(es): 49.0001 Routing for area address(es): 49.0001 Interfaces supported by IS-IS: FastEthernet1/0 - IP - IPv6 FastEthernet0/1 - IP - IPv6 FastEthernet0/0 - IP - IPv6 Passive interface: Loopback0 Redistribute: static (on by default) Distance for L2 CLNS routes: 110 RRR level: none Generate narrow metrics: level-1-2 Accept narrow metrics: level-1-2 Generate wide metrics: none Accept wide metrics: none R5#show clns protocol IS-IS Router: 1 System Id: 1921.6800.1005.00 IS-Type: level-1-2 Manual area address(es): 49.0002 Routing for area address(es): 49.0002 Interfaces supported by IS-IS: FastEthernet1/0 - IP - IPv6 FastEthernet0/1 - IP - IPv6 FastEthernet0/0 - IP - IPv6 Passive interface: Loopback0 Redistribute: static (on by default) Distance for L2 CLNS routes: 110 RRR level: none Generate narrow metrics: level-1-2 Accept narrow metrics: level-1-2 Generate wide metrics: none Accept wide metrics: none R6#show clns protocol IS-IS Router: 1 System Id: 1921.6800.1006.00 IS-Type: level-1-2 Manual area address(es): 49.0002 Routing for area address(es): 49.0002 Interfaces supported by IS-IS: FastEthernet1/0 - IP - IPv6 FastEthernet0/1 - IP - IPv6 FastEthernet0/0 - IP - IPv6 Passive interface: Loopback0 Redistribute: static (on by default) Distance for L2 CLNS routes: 110 RRR level: none Generate narrow metrics: level-1-2 Accept narrow metrics: level-1-2 Generate wide metrics: none Accept wide metrics: none R7#show clns protocol IS-IS Router: 1 System Id: 1921.6800.1007.00 IS-Type: level-1 Manual area address(es): 49.0002 Routing for area address(es): 49.0002 Interfaces supported by IS-IS: FastEthernet0/1 - IP - IPv6 FastEthernet0/0 - IP - IPv6 Passive interface: Loopback0 Redistribute: static (on by default) Distance for L2 CLNS routes: 110 RRR level: none Generate narrow metrics: level-1-2 Accept narrow metrics: level-1-2 Generate wide metrics: none Accept wide metrics: none R8#show clns protocol IS-IS Router: 1 System Id: 1921.6800.1008.00 IS-Type: level-1-2 Manual area address(es): 49.0003 Routing for area address(es): 49.0003 Interfaces supported by IS-IS: FastEthernet0/1 - IP - IPv6 FastEthernet0/0 - IP - IPv6 Passive interface: Loopback0 Redistribute: static (on by default) Distance for L2 CLNS routes: 110 TID 0: Inter-area IP routes from L2 into L1 enabled with list 100 RRR level: none Generate narrow metrics: level-1-2 Accept narrow metrics: level-1-2 Generate wide metrics: none Accept wide metrics: none R9#show clns protocol IS-IS Router: 1 System Id: 1921.6800.1009.00 IS-Type: level-1 Manual area address(es): 49.0003 Routing for area address(es): 49.0003 Interfaces supported by IS-IS: FastEthernet0/0 - IP - IPv6 Passive interface: Loopback0 Redistribute: static (on by default) Distance for L2 CLNS routes: 110 RRR level: none Generate narrow metrics: level-1-2 Accept narrow metrics: level-1-2 Generate wide metrics: none Accept wide metrics: none
Routing
R1#show ipv6 route IPv6 Routing Table - default - 28 entries Codes: C - Connected, L - Local, S - Static, U - Per-user Static route B - BGP, HA - Home Agent, MR - Mobile Router, R - RIP H - NHRP, I1 - ISIS L1, I2 - ISIS L2, IA - ISIS interarea IS - ISIS summary, D - EIGRP, EX - EIGRP external, NM - NEMO ND - ND Default, NDp - ND Prefix, DCE - Destination, NDr - Redirect O - OSPF Intra, OI - OSPF Inter, OE1 - OSPF ext 1, OE2 - OSPF ext 2 ON1 - OSPF NSSA ext 1, ON2 - OSPF NSSA ext 2, l - LISP I2 2001:10:1:24::/64 [115/20] via FE80::C805:30FF:FE9C:8, FastEthernet0/0 I2 2001:10:1:25::/64 [115/20] via FE80::C805:30FF:FE9C:8, FastEthernet0/0 I2 2001:10:1:34::/64 [115/20] via FE80::C807:8FF:FE08:8, FastEthernet0/0 I2 2001:10:1:38::/64 [115/20] via FE80::C807:8FF:FE08:8, FastEthernet0/0 I2 2001:10:1:46::/64 [115/30] via FE80::C805:30FF:FE9C:8, FastEthernet0/0 via FE80::C807:8FF:FE08:8, FastEthernet0/0 I2 2001:10:1:56::/64 [115/30] via FE80::C805:30FF:FE9C:8, FastEthernet0/0 I2 2001:10:1:57::/64 [115/30] via FE80::C805:30FF:FE9C:8, FastEthernet0/0 I2 2001:10:1:67::/64 [115/40] via FE80::C805:30FF:FE9C:8, FastEthernet0/0 via FE80::C807:8FF:FE08:8, FastEthernet0/0 I2 2001:10:1:89::/64 [115/30] via FE80::C807:8FF:FE08:8, FastEthernet0/0 C 2001:10:1:123::/64 [0/0] via FastEthernet0/0, directly connected L 2001:10:1:123::1/128 [0/0] via FastEthernet0/0, receive O 2001:172:16::/64 [110/2] via FE80::C809:1DFF:FED4:6, FastEthernet0/1 O 2001:172:16:1::/64 [110/2] via FE80::C809:1DFF:FED4:6, FastEthernet0/1 O 2001:172:16:2::/64 [110/2] via FE80::C809:1DFF:FED4:6, FastEthernet0/1 O 2001:172:16:3::/64 [110/2] via FE80::C809:1DFF:FED4:6, FastEthernet0/1 C 2001:172:16:110::/64 [0/0] via FastEthernet0/1, directly connected L 2001:172:16:110::1/128 [0/0] via FastEthernet0/1, receive LC 2001:192:168:1::1/128 [0/0] via Loopback0, receive I2 2001:192:168:1::2/128 [115/10] via FE80::C805:30FF:FE9C:8, FastEthernet0/0 I2 2001:192:168:1::3/128 [115/10] via FE80::C807:8FF:FE08:8, FastEthernet0/0 I2 2001:192:168:1::4/128 [115/20] via FE80::C805:30FF:FE9C:8, FastEthernet0/0 via FE80::C807:8FF:FE08:8, FastEthernet0/0 I2 2001:192:168:1::5/128 [115/20] via FE80::C805:30FF:FE9C:8, FastEthernet0/0 I2 2001:192:168:1::6/128 [115/30] via FE80::C805:30FF:FE9C:8, FastEthernet0/0 via FE80::C807:8FF:FE08:8, FastEthernet0/0 I2 2001:192:168:1::7/128 [115/30] via FE80::C805:30FF:FE9C:8, FastEthernet0/0 I2 2001:192:168:1::8/128 [115/20] via FE80::C807:8FF:FE08:8, FastEthernet0/0 I2 2001:192:168:1::9/128 [115/30] via FE80::C807:8FF:FE08:8, FastEthernet0/0 O 2001:192:168:1::10/128 [110/1] via FE80::C809:1DFF:FED4:6, FastEthernet0/1 L FF00::/8 [0/0] via Null0, receive R2#show ipv6 route IPv6 Routing Table - default - 28 entries Codes: C - Connected, L - Local, S - Static, U - Per-user Static route B - BGP, HA - Home Agent, MR - Mobile Router, R - RIP H - NHRP, I1 - ISIS L1, I2 - ISIS L2, IA - ISIS interarea IS - ISIS summary, D - EIGRP, EX - EIGRP external, NM - NEMO ND - ND Default, NDp - ND Prefix, DCE - Destination, NDr - Redirect O - OSPF Intra, OI - OSPF Inter, OE1 - OSPF ext 1, OE2 - OSPF ext 2 ON1 - OSPF NSSA ext 1, ON2 - OSPF NSSA ext 2, l - LISP C 2001:10:1:24::/64 [0/0] via FastEthernet1/0, directly connected L 2001:10:1:24::2/128 [0/0] via FastEthernet1/0, receive C 2001:10:1:25::/64 [0/0] via FastEthernet0/1, directly connected L 2001:10:1:25::2/128 [0/0] via FastEthernet0/1, receive I2 2001:10:1:34::/64 [115/20] via FE80::C807:8FF:FE08:8, FastEthernet0/0 via FE80::C806:8FF:FE08:1C, FastEthernet1/0 I2 2001:10:1:38::/64 [115/20] via FE80::C807:8FF:FE08:8, FastEthernet0/0 I2 2001:10:1:46::/64 [115/20] via FE80::C806:8FF:FE08:1C, FastEthernet1/0 I2 2001:10:1:56::/64 [115/20] via FE80::C800:11FF:FEB0:6, FastEthernet0/1 I2 2001:10:1:57::/64 [115/20] via FE80::C800:11FF:FEB0:6, FastEthernet0/1 I2 2001:10:1:67::/64 [115/30] via FE80::C800:11FF:FEB0:6, FastEthernet0/1 via FE80::C806:8FF:FE08:1C, FastEthernet1/0 I2 2001:10:1:89::/64 [115/30] via FE80::C807:8FF:FE08:8, FastEthernet0/0 C 2001:10:1:123::/64 [0/0] via FastEthernet0/0, directly connected L 2001:10:1:123::2/128 [0/0] via FastEthernet0/0, receive I2 2001:172:16::/64 [115/10] via FE80::C804:30FF:FE9C:8, FastEthernet0/0 I2 2001:172:16:1::/64 [115/10] via FE80::C804:30FF:FE9C:8, FastEthernet0/0 I2 2001:172:16:2::/64 [115/10] via FE80::C804:30FF:FE9C:8, FastEthernet0/0 I2 2001:172:16:3::/64 [115/10] via FE80::C804:30FF:FE9C:8, FastEthernet0/0 I2 2001:192:168:1::1/128 [115/10] via FE80::C804:30FF:FE9C:8, FastEthernet0/0 LC 2001:192:168:1::2/128 [0/0] via Loopback0, receive I2 2001:192:168:1::3/128 [115/10] via FE80::C807:8FF:FE08:8, FastEthernet0/0 I2 2001:192:168:1::4/128 [115/10] via FE80::C806:8FF:FE08:1C, FastEthernet1/0 I2 2001:192:168:1::5/128 [115/10] via FE80::C800:11FF:FEB0:6, FastEthernet0/1 I2 2001:192:168:1::6/128 [115/20] via FE80::C800:11FF:FEB0:6, FastEthernet0/1 via FE80::C806:8FF:FE08:1C, FastEthernet1/0 I2 2001:192:168:1::7/128 [115/20] via FE80::C800:11FF:FEB0:6, FastEthernet0/1 I2 2001:192:168:1::8/128 [115/20] via FE80::C807:8FF:FE08:8, FastEthernet0/0 I2 2001:192:168:1::9/128 [115/30] via FE80::C807:8FF:FE08:8, FastEthernet0/0 I2 2001:192:168:1::10/128 [115/10] via FE80::C804:30FF:FE9C:8, FastEthernet0/0 L FF00::/8 [0/0] via Null0, receive R3#show ipv6 route IPv6 Routing Table - default - 28 entries Codes: C - Connected, L - Local, S - Static, U - Per-user Static route B - BGP, HA - Home Agent, MR - Mobile Router, R - RIP H - NHRP, I1 - ISIS L1, I2 - ISIS L2, IA - ISIS interarea IS - ISIS summary, D - EIGRP, EX - EIGRP external, NM - NEMO ND - ND Default, NDp - ND Prefix, DCE - Destination, NDr - Redirect O - OSPF Intra, OI - OSPF Inter, OE1 - OSPF ext 1, OE2 - OSPF ext 2 ON1 - OSPF NSSA ext 1, ON2 - OSPF NSSA ext 2, l - LISP I2 2001:10:1:24::/64 [115/20] via FE80::C806:8FF:FE08:8, FastEthernet1/0 via FE80::C805:30FF:FE9C:8, FastEthernet0/0 I2 2001:10:1:25::/64 [115/20] via FE80::C805:30FF:FE9C:8, FastEthernet0/0 C 2001:10:1:34::/64 [0/0] via FastEthernet1/0, directly connected L 2001:10:1:34::3/128 [0/0] via FastEthernet1/0, receive C 2001:10:1:38::/64 [0/0] via FastEthernet0/1, directly connected L 2001:10:1:38::3/128 [0/0] via FastEthernet0/1, receive I2 2001:10:1:46::/64 [115/20] via FE80::C806:8FF:FE08:8, FastEthernet1/0 I2 2001:10:1:56::/64 [115/30] via FE80::C806:8FF:FE08:8, FastEthernet1/0 via FE80::C805:30FF:FE9C:8, FastEthernet0/0 I2 2001:10:1:57::/64 [115/30] via FE80::C805:30FF:FE9C:8, FastEthernet0/0 I2 2001:10:1:67::/64 [115/30] via FE80::C806:8FF:FE08:8, FastEthernet1/0 I2 2001:10:1:89::/64 [115/20] via FE80::C803:19FF:FE84:6, FastEthernet0/1 C 2001:10:1:123::/64 [0/0] via FastEthernet0/0, directly connected L 2001:10:1:123::3/128 [0/0] via FastEthernet0/0, receive I2 2001:172:16::/64 [115/10] via FE80::C804:30FF:FE9C:8, FastEthernet0/0 I2 2001:172:16:1::/64 [115/10] via FE80::C804:30FF:FE9C:8, FastEthernet0/0 I2 2001:172:16:2::/64 [115/10] via FE80::C804:30FF:FE9C:8, FastEthernet0/0 I2 2001:172:16:3::/64 [115/10] via FE80::C804:30FF:FE9C:8, FastEthernet0/0 I2 2001:192:168:1::1/128 [115/10] via FE80::C804:30FF:FE9C:8, FastEthernet0/0 I2 2001:192:168:1::2/128 [115/10] via FE80::C805:30FF:FE9C:8, FastEthernet0/0 LC 2001:192:168:1::3/128 [0/0] via Loopback0, receive I2 2001:192:168:1::4/128 [115/10] via FE80::C806:8FF:FE08:8, FastEthernet1/0 I2 2001:192:168:1::5/128 [115/20] via FE80::C805:30FF:FE9C:8, FastEthernet0/0 I2 2001:192:168:1::6/128 [115/20] via FE80::C806:8FF:FE08:8, FastEthernet1/0 I2 2001:192:168:1::7/128 [115/30] via FE80::C805:30FF:FE9C:8, FastEthernet0/0 via FE80::C806:8FF:FE08:8, FastEthernet1/0 I2 2001:192:168:1::8/128 [115/10] via FE80::C803:19FF:FE84:6, FastEthernet0/1 I2 2001:192:168:1::9/128 [115/20] via FE80::C803:19FF:FE84:6, FastEthernet0/1 I2 2001:192:168:1::10/128 [115/10] via FE80::C804:30FF:FE9C:8, FastEthernet0/0 L FF00::/8 [0/0] via Null0, receive R4#show ipv6 route IPv6 Routing Table - default - 28 entries Codes: C - Connected, L - Local, S - Static, U - Per-user Static route B - BGP, HA - Home Agent, MR - Mobile Router, R - RIP H - NHRP, I1 - ISIS L1, I2 - ISIS L2, IA - ISIS interarea IS - ISIS summary, D - EIGRP, EX - EIGRP external, NM - NEMO ND - ND Default, NDp - ND Prefix, DCE - Destination, NDr - Redirect O - OSPF Intra, OI - OSPF Inter, OE1 - OSPF ext 1, OE2 - OSPF ext 2 ON1 - OSPF NSSA ext 1, ON2 - OSPF NSSA ext 2, l - LISP C 2001:10:1:24::/64 [0/0] via FastEthernet1/0, directly connected L 2001:10:1:24::4/128 [0/0] via FastEthernet1/0, receive I2 2001:10:1:25::/64 [115/20] via FE80::C805:30FF:FE9C:1C, FastEthernet1/0 C 2001:10:1:34::/64 [0/0] via FastEthernet0/0, directly connected L 2001:10:1:34::4/128 [0/0] via FastEthernet0/0, receive I2 2001:10:1:38::/64 [115/20] via FE80::C807:8FF:FE08:1C, FastEthernet0/0 C 2001:10:1:46::/64 [0/0] via FastEthernet0/1, directly connected L 2001:10:1:46::4/128 [0/0] via FastEthernet0/1, receive I2 2001:10:1:56::/64 [115/20] via FE80::C801:11FF:FEB0:6, FastEthernet0/1 I2 2001:10:1:57::/64 [115/30] via FE80::C801:11FF:FEB0:6, FastEthernet0/1 via FE80::C805:30FF:FE9C:1C, FastEthernet1/0 I2 2001:10:1:67::/64 [115/20] via FE80::C801:11FF:FEB0:6, FastEthernet0/1 I2 2001:10:1:89::/64 [115/30] via FE80::C807:8FF:FE08:1C, FastEthernet0/0 I2 2001:10:1:123::/64 [115/20] via FE80::C807:8FF:FE08:1C, FastEthernet0/0 via FE80::C805:30FF:FE9C:1C, FastEthernet1/0 I2 2001:172:16::/64 [115/20] via FE80::C805:30FF:FE9C:1C, FastEthernet1/0 via FE80::C807:8FF:FE08:1C, FastEthernet0/0 I2 2001:172:16:1::/64 [115/20] via FE80::C805:30FF:FE9C:1C, FastEthernet1/0 via FE80::C807:8FF:FE08:1C, FastEthernet0/0 I2 2001:172:16:2::/64 [115/20] via FE80::C805:30FF:FE9C:1C, FastEthernet1/0 via FE80::C807:8FF:FE08:1C, FastEthernet0/0 I2 2001:172:16:3::/64 [115/20] via FE80::C805:30FF:FE9C:1C, FastEthernet1/0 via FE80::C807:8FF:FE08:1C, FastEthernet0/0 I2 2001:192:168:1::1/128 [115/20] via FE80::C807:8FF:FE08:1C, FastEthernet0/0 via FE80::C805:30FF:FE9C:1C, FastEthernet1/0 I2 2001:192:168:1::2/128 [115/10] via FE80::C805:30FF:FE9C:1C, FastEthernet1/0 I2 2001:192:168:1::3/128 [115/10] via FE80::C807:8FF:FE08:1C, FastEthernet0/0 LC 2001:192:168:1::4/128 [0/0] via Loopback0, receive I2 2001:192:168:1::5/128 [115/20] via FE80::C801:11FF:FEB0:6, FastEthernet0/1 via FE80::C805:30FF:FE9C:1C, FastEthernet1/0 I2 2001:192:168:1::6/128 [115/10] via FE80::C801:11FF:FEB0:6, FastEthernet0/1 I2 2001:192:168:1::7/128 [115/20] via FE80::C801:11FF:FEB0:6, FastEthernet0/1 I2 2001:192:168:1::8/128 [115/20] via FE80::C807:8FF:FE08:1C, FastEthernet0/0 I2 2001:192:168:1::9/128 [115/30] via FE80::C807:8FF:FE08:1C, FastEthernet0/0 I2 2001:192:168:1::10/128 [115/20] via FE80::C805:30FF:FE9C:1C, FastEthernet1/0 via FE80::C807:8FF:FE08:1C, FastEthernet0/0 L FF00::/8 [0/0] via Null0, receive R5#show ipv6 route IPv6 Routing Table - default - 28 entries Codes: C - Connected, L - Local, S - Static, U - Per-user Static route B - BGP, HA - Home Agent, MR - Mobile Router, R - RIP H - NHRP, I1 - ISIS L1, I2 - ISIS L2, IA - ISIS interarea IS - ISIS summary, D - EIGRP, EX - EIGRP external, NM - NEMO ND - ND Default, NDp - ND Prefix, DCE - Destination, NDr - Redirect O - OSPF Intra, OI - OSPF Inter, OE1 - OSPF ext 1, OE2 - OSPF ext 2 ON1 - OSPF NSSA ext 1, ON2 - OSPF NSSA ext 2, l - LISP I2 2001:10:1:24::/64 [115/20] via FE80::C805:30FF:FE9C:6, FastEthernet0/1 C 2001:10:1:25::/64 [0/0] via FastEthernet0/1, directly connected L 2001:10:1:25::5/128 [0/0] via FastEthernet0/1, receive I2 2001:10:1:34::/64 [115/30] via FE80::C805:30FF:FE9C:6, FastEthernet0/1 via FE80::C801:11FF:FEB0:1C, FastEthernet1/0 I2 2001:10:1:38::/64 [115/30] via FE80::C805:30FF:FE9C:6, FastEthernet0/1 I1 2001:10:1:46::/64 [115/20] via FE80::C801:11FF:FEB0:1C, FastEthernet1/0 C 2001:10:1:56::/64 [0/0] via FastEthernet1/0, directly connected L 2001:10:1:56::5/128 [0/0] via FastEthernet1/0, receive C 2001:10:1:57::/64 [0/0] via FastEthernet0/0, directly connected L 2001:10:1:57::5/128 [0/0] via FastEthernet0/0, receive I1 2001:10:1:67::/64 [115/20] via FE80::C801:11FF:FEB0:1C, FastEthernet1/0 I2 2001:10:1:89::/64 [115/40] via FE80::C805:30FF:FE9C:6, FastEthernet0/1 I2 2001:10:1:123::/64 [115/20] via FE80::C805:30FF:FE9C:6, FastEthernet0/1 I2 2001:172:16::/64 [115/20] via FE80::C805:30FF:FE9C:6, FastEthernet0/1 I2 2001:172:16:1::/64 [115/20] via FE80::C805:30FF:FE9C:6, FastEthernet0/1 I2 2001:172:16:2::/64 [115/20] via FE80::C805:30FF:FE9C:6, FastEthernet0/1 I2 2001:172:16:3::/64 [115/20] via FE80::C805:30FF:FE9C:6, FastEthernet0/1 I2 2001:192:168:1::1/128 [115/20] via FE80::C805:30FF:FE9C:6, FastEthernet0/1 I2 2001:192:168:1::2/128 [115/10] via FE80::C805:30FF:FE9C:6, FastEthernet0/1 I2 2001:192:168:1::3/128 [115/20] via FE80::C805:30FF:FE9C:6, FastEthernet0/1 I2 2001:192:168:1::4/128 [115/20] via FE80::C805:30FF:FE9C:6, FastEthernet0/1 via FE80::C801:11FF:FEB0:1C, FastEthernet1/0 LC 2001:192:168:1::5/128 [0/0] via Loopback0, receive I1 2001:192:168:1::6/128 [115/10] via FE80::C801:11FF:FEB0:1C, FastEthernet1/0 I1 2001:192:168:1::7/128 [115/10] via FE80::C802:19FF:FE84:8, FastEthernet0/0 I2 2001:192:168:1::8/128 [115/30] via FE80::C805:30FF:FE9C:6, FastEthernet0/1 I2 2001:192:168:1::9/128 [115/40] via FE80::C805:30FF:FE9C:6, FastEthernet0/1 I2 2001:192:168:1::10/128 [115/20] via FE80::C805:30FF:FE9C:6, FastEthernet0/1 L FF00::/8 [0/0] via Null0, receive R6#show ipv6 route IPv6 Routing Table - default - 28 entries Codes: C - Connected, L - Local, S - Static, U - Per-user Static route B - BGP, HA - Home Agent, MR - Mobile Router, R - RIP H - NHRP, I1 - ISIS L1, I2 - ISIS L2, IA - ISIS interarea IS - ISIS summary, D - EIGRP, EX - EIGRP external, NM - NEMO ND - ND Default, NDp - ND Prefix, DCE - Destination, NDr - Redirect O - OSPF Intra, OI - OSPF Inter, OE1 - OSPF ext 1, OE2 - OSPF ext 2 ON1 - OSPF NSSA ext 1, ON2 - OSPF NSSA ext 2, l - LISP I2 2001:10:1:24::/64 [115/20] via FE80::C806:8FF:FE08:6, FastEthernet0/1 I1 2001:10:1:25::/64 [115/20] via FE80::C800:11FF:FEB0:1C, FastEthernet1/0 I2 2001:10:1:34::/64 [115/20] via FE80::C806:8FF:FE08:6, FastEthernet0/1 I2 2001:10:1:38::/64 [115/30] via FE80::C806:8FF:FE08:6, FastEthernet0/1 C 2001:10:1:46::/64 [0/0] via FastEthernet0/1, directly connected L 2001:10:1:46::6/128 [0/0] via FastEthernet0/1, receive C 2001:10:1:56::/64 [0/0] via FastEthernet1/0, directly connected L 2001:10:1:56::6/128 [0/0] via FastEthernet1/0, receive I1 2001:10:1:57::/64 [115/20] via FE80::C800:11FF:FEB0:1C, FastEthernet1/0 via FE80::C802:19FF:FE84:6, FastEthernet0/0 C 2001:10:1:67::/64 [0/0] via FastEthernet0/0, directly connected L 2001:10:1:67::6/128 [0/0] via FastEthernet0/0, receive I2 2001:10:1:89::/64 [115/40] via FE80::C806:8FF:FE08:6, FastEthernet0/1 I2 2001:10:1:123::/64 [115/30] via FE80::C800:11FF:FEB0:1C, FastEthernet1/0 via FE80::C806:8FF:FE08:6, FastEthernet0/1 I2 2001:172:16::/64 [115/30] via FE80::C806:8FF:FE08:6, FastEthernet0/1 via FE80::C800:11FF:FEB0:1C, FastEthernet1/0 I2 2001:172:16:1::/64 [115/30] via FE80::C806:8FF:FE08:6, FastEthernet0/1 via FE80::C800:11FF:FEB0:1C, FastEthernet1/0 I2 2001:172:16:2::/64 [115/30] via FE80::C806:8FF:FE08:6, FastEthernet0/1 via FE80::C800:11FF:FEB0:1C, FastEthernet1/0 I2 2001:172:16:3::/64 [115/30] via FE80::C806:8FF:FE08:6, FastEthernet0/1 via FE80::C800:11FF:FEB0:1C, FastEthernet1/0 I2 2001:192:168:1::1/128 [115/30] via FE80::C800:11FF:FEB0:1C, FastEthernet1/0 via FE80::C806:8FF:FE08:6, FastEthernet0/1 I2 2001:192:168:1::2/128 [115/20] via FE80::C800:11FF:FEB0:1C, FastEthernet1/0 via FE80::C806:8FF:FE08:6, FastEthernet0/1 I2 2001:192:168:1::3/128 [115/20] via FE80::C806:8FF:FE08:6, FastEthernet0/1 I2 2001:192:168:1::4/128 [115/10] via FE80::C806:8FF:FE08:6, FastEthernet0/1 I1 2001:192:168:1::5/128 [115/10] via FE80::C800:11FF:FEB0:1C, FastEthernet1/0 LC 2001:192:168:1::6/128 [0/0] via Loopback0, receive I1 2001:192:168:1::7/128 [115/10] via FE80::C802:19FF:FE84:6, FastEthernet0/0 I2 2001:192:168:1::8/128 [115/30] via FE80::C806:8FF:FE08:6, FastEthernet0/1 I2 2001:192:168:1::9/128 [115/40] via FE80::C806:8FF:FE08:6, FastEthernet0/1 I2 2001:192:168:1::10/128 [115/30] via FE80::C806:8FF:FE08:6, FastEthernet0/1 via FE80::C800:11FF:FEB0:1C, FastEthernet1/0 L FF00::/8 [0/0] via Null0, receive R7#show ipv6 route IPv6 Routing Table - default - 12 entries Codes: C - Connected, L - Local, S - Static, U - Per-user Static route B - BGP, HA - Home Agent, MR - Mobile Router, R - RIP H - NHRP, I1 - ISIS L1, I2 - ISIS L2, IA - ISIS interarea IS - ISIS summary, D - EIGRP, EX - EIGRP external, NM - NEMO ND - ND Default, NDp - ND Prefix, DCE - Destination, NDr - Redirect O - OSPF Intra, OI - OSPF Inter, OE1 - OSPF ext 1, OE2 - OSPF ext 2 ON1 - OSPF NSSA ext 1, ON2 - OSPF NSSA ext 2, l - LISP I1 ::/0 [115/10] via FE80::C800:11FF:FEB0:8, FastEthernet0/0 I1 2001:10:1:25::/64 [115/20] via FE80::C800:11FF:FEB0:8, FastEthernet0/0 I1 2001:10:1:46::/64 [115/30] via FE80::C800:11FF:FEB0:8, FastEthernet0/0 via FE80::C801:11FF:FEB0:8, FastEthernet0/1 I1 2001:10:1:56::/64 [115/20] via FE80::C800:11FF:FEB0:8, FastEthernet0/0 C 2001:10:1:57::/64 [0/0] via FastEthernet0/0, directly connected L 2001:10:1:57::7/128 [0/0] via FastEthernet0/0, receive C 2001:10:1:67::/64 [0/0] via FastEthernet0/1, directly connected L 2001:10:1:67::7/128 [0/0] via FastEthernet0/1, receive I1 2001:192:168:1::5/128 [115/10] via FE80::C800:11FF:FEB0:8, FastEthernet0/0 I1 2001:192:168:1::6/128 [115/20] via FE80::C800:11FF:FEB0:8, FastEthernet0/0 via FE80::C801:11FF:FEB0:8, FastEthernet0/1 LC 2001:192:168:1::7/128 [0/0] via Loopback0, receive L FF00::/8 [0/0] via Null0, receive R8#show ipv6 route IPv6 Routing Table - default - 28 entries Codes: C - Connected, L - Local, S - Static, U - Per-user Static route B - BGP, HA - Home Agent, MR - Mobile Router, R - RIP H - NHRP, I1 - ISIS L1, I2 - ISIS L2, IA - ISIS interarea IS - ISIS summary, D - EIGRP, EX - EIGRP external, NM - NEMO ND - ND Default, NDp - ND Prefix, DCE - Destination, NDr - Redirect O - OSPF Intra, OI - OSPF Inter, OE1 - OSPF ext 1, OE2 - OSPF ext 2 ON1 - OSPF NSSA ext 1, ON2 - OSPF NSSA ext 2, l - LISP I2 2001:10:1:24::/64 [115/30] via FE80::C807:8FF:FE08:6, FastEthernet0/1 I2 2001:10:1:25::/64 [115/30] via FE80::C807:8FF:FE08:6, FastEthernet0/1 I2 2001:10:1:34::/64 [115/20] via FE80::C807:8FF:FE08:6, FastEthernet0/1 C 2001:10:1:38::/64 [0/0] via FastEthernet0/1, directly connected L 2001:10:1:38::8/128 [0/0] via FastEthernet0/1, receive I2 2001:10:1:46::/64 [115/30] via FE80::C807:8FF:FE08:6, FastEthernet0/1 I2 2001:10:1:56::/64 [115/40] via FE80::C807:8FF:FE08:6, FastEthernet0/1 I2 2001:10:1:57::/64 [115/40] via FE80::C807:8FF:FE08:6, FastEthernet0/1 I2 2001:10:1:67::/64 [115/40] via FE80::C807:8FF:FE08:6, FastEthernet0/1 C 2001:10:1:89::/64 [0/0] via FastEthernet0/0, directly connected L 2001:10:1:89::8/128 [0/0] via FastEthernet0/0, receive I2 2001:10:1:123::/64 [115/20] via FE80::C807:8FF:FE08:6, FastEthernet0/1 IS 2001:172:16::/48 [115/20] via Null0, directly connected I2 2001:172:16::/64 [115/20] via FE80::C807:8FF:FE08:6, FastEthernet0/1 I2 2001:172:16:1::/64 [115/20] via FE80::C807:8FF:FE08:6, FastEthernet0/1 I2 2001:172:16:2::/64 [115/20] via FE80::C807:8FF:FE08:6, FastEthernet0/1 I2 2001:172:16:3::/64 [115/20] via FE80::C807:8FF:FE08:6, FastEthernet0/1 I2 2001:192:168:1::1/128 [115/20] via FE80::C807:8FF:FE08:6, FastEthernet0/1 I2 2001:192:168:1::2/128 [115/20] via FE80::C807:8FF:FE08:6, FastEthernet0/1 I2 2001:192:168:1::3/128 [115/10] via FE80::C807:8FF:FE08:6, FastEthernet0/1 I2 2001:192:168:1::4/128 [115/20] via FE80::C807:8FF:FE08:6, FastEthernet0/1 I2 2001:192:168:1::5/128 [115/30] via FE80::C807:8FF:FE08:6, FastEthernet0/1 I2 2001:192:168:1::6/128 [115/30] via FE80::C807:8FF:FE08:6, FastEthernet0/1 I2 2001:192:168:1::7/128 [115/40] via FE80::C807:8FF:FE08:6, FastEthernet0/1 LC 2001:192:168:1::8/128 [0/0] via Loopback0, receive I1 2001:192:168:1::9/128 [115/10] via FE80::C808:1DFF:FED4:8, FastEthernet0/0 I2 2001:192:168:1::10/128 [115/20] via FE80::C807:8FF:FE08:6, FastEthernet0/1 L FF00::/8 [0/0] via Null0, receive R8#show isis database detail Tag 1: IS-IS Level-1 Link State Database: LSPID LSP Seq Num LSP Checksum LSP Holdtime ATT/P/OL R8.00-00 * 0x00000006 0x37C1 668 1/0/0 Area Address: 49.0003 NLPID: 0xCC 0x8E Hostname: R8 IP Address: 192.168.1.8 Metric: 10 IP 10.1.89.0 255.255.255.0 Metric: 10 IP 10.1.38.0 255.255.255.0 Metric: 0 IP 192.168.1.8 255.255.255.255 IPv6 Address: 2001:192:168:1::8 Metric: 10 IPv6 2001:10:1:89::/64 Metric: 10 IPv6 2001:10:1:38::/64 Metric: 0 IPv6 2001:192:168:1::8/128 Metric: 10 IS R9.01 Metric: 158 IP-Interarea 10.1.24.0 255.255.255.0 Metric: 158 IP-Interarea 10.1.25.0 255.255.255.0 Metric: 148 IP-Interarea 10.1.34.0 255.255.255.0 Metric: 158 IP-Interarea 10.1.46.0 255.255.255.0 Metric: 168 IP-Interarea 10.1.56.0 255.255.255.0 Metric: 168 IP-Interarea 10.1.57.0 255.255.255.0 Metric: 168 IP-Interarea 10.1.67.0 255.255.255.0 Metric: 148 IP-Interarea 10.1.123.0 255.255.255.0 Metric: 148 IP-Interarea 172.16.110.0 255.255.255.0 Metric: 148 IP-Interarea 192.168.1.1 255.255.255.255 Metric: 148 IP-Interarea 192.168.1.2 255.255.255.255 Metric: 138 IP-Interarea 192.168.1.3 255.255.255.255 Metric: 148 IP-Interarea 192.168.1.4 255.255.255.255 Metric: 158 IP-Interarea 192.168.1.5 255.255.255.255 Metric: 158 IP-Interarea 192.168.1.6 255.255.255.255 Metric: 168 IP-Interarea 192.168.1.7 255.255.255.255 Metric: 148 IP-Interarea 192.168.1.10 255.255.255.255 Metric: 148 IP-Interarea 172.16.0.0 255.255.252.0 Metric: 30 IPv6-Interarea 2001:10:1:24::/64 Metric: 30 IPv6-Interarea 2001:10:1:25::/64 Metric: 20 IPv6-Interarea 2001:10:1:34::/64 Metric: 30 IPv6-Interarea 2001:10:1:46::/64 Metric: 40 IPv6-Interarea 2001:10:1:56::/64 Metric: 40 IPv6-Interarea 2001:10:1:57::/64 Metric: 40 IPv6-Interarea 2001:10:1:67::/64 Metric: 20 IPv6-Interarea 2001:10:1:123::/64 Metric: 20 IPv6-Interarea 2001:192:168:1::1/128 Metric: 20 IPv6-Interarea 2001:192:168:1::2/128 Metric: 10 IPv6-Interarea 2001:192:168:1::3/128 Metric: 20 IPv6-Interarea 2001:192:168:1::4/128 Metric: 30 IPv6-Interarea 2001:192:168:1::5/128 Metric: 30 IPv6-Interarea 2001:192:168:1::6/128 Metric: 40 IPv6-Interarea 2001:192:168:1::7/128 Metric: 20 IPv6-Interarea 2001:192:168:1::10/128 Metric: 20 IPv6-Interarea 2001:172:16::/48 R9.00-00 0x00000002 0x81C4 623 0/0/0 Area Address: 49.0003 NLPID: 0xCC 0x8E Hostname: R9 IP Address: 192.168.1.9 Metric: 10 IP 10.1.89.0 255.255.255.0 Metric: 0 IP 192.168.1.9 255.255.255.255 IPv6 Address: 2001:192:168:1::9 Metric: 10 IPv6 2001:10:1:89::/64 Metric: 0 IPv6 2001:192:168:1::9/128 Metric: 10 IS R9.01 R9.01-00 0x00000001 0x180E 624 0/0/0 Metric: 0 IS R9.00 Metric: 0 IS R8.00 IS-IS Level-2 Link State Database: LSPID LSP Seq Num LSP Checksum LSP Holdtime ATT/P/OL R1.00-00 0x00000006 0xBEDD 662 0/0/0 Area Address: 49.0001 NLPID: 0xCC 0x8E Hostname: R1 IP Address: 192.168.1.1 IPv6 Address: 2001:192:168:1::1 Metric: 10 IS R3.01 Metric: 10 IP 10.1.123.0 255.255.255.0 Metric: 0 IP-External 172.16.0.0 255.255.255.0 Metric: 0 IP-External 172.16.1.0 255.255.255.0 Metric: 0 IP-External 172.16.2.0 255.255.255.0 Metric: 0 IP-External 172.16.3.0 255.255.255.0 Metric: 0 IP-External 172.16.110.0 255.255.255.0 Metric: 0 IP 192.168.1.1 255.255.255.255 Metric: 0 IP-External 192.168.1.10 255.255.255.255 Metric: 10 IPv6 2001:10:1:123::/64 Metric: 0 IPv6 2001:192:168:1::1/128 Metric: 0 IPv6 2001:172:16::/64 Metric: 0 IPv6 2001:172:16:1::/64 Metric: 0 IPv6 2001:172:16:2::/64 Metric: 0 IPv6 2001:172:16:3::/64 Metric: 0 IPv6 2001:192:168:1::10/128 R2.00-00 0x00000005 0xB98A 634 0/0/0 Area Address: 49.0001 NLPID: 0xCC 0x8E Hostname: R2 IP Address: 192.168.1.2 IPv6 Address: 2001:192:168:1::2 Metric: 10 IS R2.02 Metric: 10 IS R3.01 Metric: 10 IS R4.03 Metric: 10 IP 10.1.24.0 255.255.255.0 Metric: 10 IP 10.1.25.0 255.255.255.0 Metric: 10 IP 10.1.123.0 255.255.255.0 Metric: 0 IP 192.168.1.2 255.255.255.255 Metric: 10 IPv6 2001:10:1:123::/64 Metric: 10 IPv6 2001:10:1:25::/64 Metric: 10 IPv6 2001:10:1:24::/64 Metric: 0 IPv6 2001:192:168:1::2/128 R2.02-00 0x00000001 0x2D8F 624 0/0/0 Metric: 0 IS R2.00 Metric: 0 IS R5.00 R3.00-00 0x00000003 0x5AAB 634 0/0/0 Area Address: 49.0001 NLPID: 0xCC 0x8E Hostname: R3 IP Address: 192.168.1.3 IPv6 Address: 2001:192:168:1::3 Metric: 10 IS R3.03 Metric: 10 IS R3.02 Metric: 10 IS R3.01 Metric: 10 IP 10.1.34.0 255.255.255.0 Metric: 10 IP 10.1.38.0 255.255.255.0 Metric: 10 IP 10.1.123.0 255.255.255.0 Metric: 0 IP 192.168.1.3 255.255.255.255 Metric: 10 IPv6 2001:10:1:123::/64 Metric: 10 IPv6 2001:10:1:38::/64 Metric: 10 IPv6 2001:10:1:34::/64 Metric: 0 IPv6 2001:192:168:1::3/128 R3.01-00 0x00000001 0xC0BD 631 0/0/0 Metric: 0 IS R3.00 Metric: 0 IS R1.00 Metric: 0 IS R2.00 R3.02-00 0x00000001 0x7E39 634 0/0/0 Metric: 0 IS R3.00 Metric: 0 IS R8.00 R3.03-00 0x00000001 0x13A7 625 0/0/0 Metric: 0 IS R3.00 Metric: 0 IS R4.00 R4.00-00 0x00000003 0x3D9E 632 0/0/0 Area Address: 49.0001 NLPID: 0xCC 0x8E Hostname: R4 IP Address: 192.168.1.4 Metric: 10 IP 10.1.34.0 255.255.255.0 Metric: 10 IP 10.1.46.0 255.255.255.0 Metric: 10 IP 10.1.24.0 255.255.255.0 IPv6 Address: 2001:192:168:1::4 Metric: 10 IPv6 2001:10:1:34::/64 Metric: 10 IPv6 2001:10:1:46::/64 Metric: 10 IPv6 2001:10:1:24::/64 Metric: 10 IS R4.03 Metric: 10 IS R4.02 Metric: 10 IS R3.03 Metric: 0 IP 192.168.1.4 255.255.255.255 Metric: 0 IPv6 2001:192:168:1::4/128 R4.02-00 0x00000001 0x5265 630 0/0/0 Metric: 0 IS R4.00 Metric: 0 IS R6.00 R4.03-00 0x00000001 0xE6D3 631 0/0/0 Metric: 0 IS R4.00 Metric: 0 IS R2.00 R5.00-00 0x00000003 0xBC3F 631 0/0/0 Area Address: 49.0002 NLPID: 0xCC 0x8E Hostname: R5 IP Address: 192.168.1.5 IPv6 Address: 2001:192:168:1::5 Metric: 10 IS R2.02 Metric: 10 IS R6.03 Metric: 10 IP 10.1.25.0 255.255.255.0 Metric: 20 IP 10.1.46.0 255.255.255.0 Metric: 10 IP 10.1.56.0 255.255.255.0 Metric: 10 IP 10.1.57.0 255.255.255.0 Metric: 20 IP 10.1.67.0 255.255.255.0 Metric: 0 IP 192.168.1.5 255.255.255.255 Metric: 10 IP 192.168.1.6 255.255.255.255 Metric: 10 IP 192.168.1.7 255.255.255.255 Metric: 10 IPv6 2001:10:1:57::/64 Metric: 10 IPv6 2001:10:1:25::/64 Metric: 10 IPv6 2001:10:1:56::/64 Metric: 0 IPv6 2001:192:168:1::5/128 Metric: 20 IPv6 2001:10:1:46::/64 Metric: 20 IPv6 2001:10:1:67::/64 Metric: 10 IPv6 2001:192:168:1::6/128 Metric: 10 IPv6 2001:192:168:1::7/128 R6.00-00 0x00000005 0x4AA9 633 0/0/0 Area Address: 49.0002 NLPID: 0xCC 0x8E Hostname: R6 IP Address: 192.168.1.6 IPv6 Address: 2001:192:168:1::6 Metric: 10 IS R6.03 Metric: 10 IS R4.02 Metric: 20 IP 10.1.25.0 255.255.255.0 Metric: 10 IP 10.1.46.0 255.255.255.0 Metric: 10 IP 10.1.56.0 255.255.255.0 Metric: 20 IP 10.1.57.0 255.255.255.0 Metric: 10 IP 10.1.67.0 255.255.255.0 Metric: 10 IP 192.168.1.5 255.255.255.255 Metric: 0 IP 192.168.1.6 255.255.255.255 Metric: 10 IP 192.168.1.7 255.255.255.255 Metric: 10 IPv6 2001:10:1:67::/64 Metric: 10 IPv6 2001:10:1:46::/64 Metric: 10 IPv6 2001:10:1:56::/64 Metric: 0 IPv6 2001:192:168:1::6/128 Metric: 20 IPv6 2001:10:1:25::/64 Metric: 20 IPv6 2001:10:1:57::/64 Metric: 10 IPv6 2001:192:168:1::5/128 Metric: 10 IPv6 2001:192:168:1::7/128 R6.03-00 0x00000001 0x3E75 619 0/0/0 Metric: 0 IS R6.00 Metric: 0 IS R5.00 R8.00-00 * 0x00000003 0x27C7 636 0/0/0 Area Address: 49.0003 NLPID: 0xCC 0x8E Hostname: R8 IP Address: 192.168.1.8 IPv6 Address: 2001:192:168:1::8 Metric: 10 IS R3.02 Metric: 10 IP 10.1.38.0 255.255.255.0 Metric: 10 IP 10.1.89.0 255.255.255.0 Metric: 0 IP 192.168.1.8 255.255.255.255 Metric: 10 IP 192.168.1.9 255.255.255.255 Metric: 10 IPv6 2001:10:1:89::/64 Metric: 10 IPv6 2001:10:1:38::/64 Metric: 0 IPv6 2001:192:168:1::8/128 Metric: 10 IPv6 2001:192:168:1::9/128 R9#show ipv6 route IPv6 Routing Table - default - 24 entries Codes: C - Connected, L - Local, S - Static, U - Per-user Static route B - BGP, HA - Home Agent, MR - Mobile Router, R - RIP H - NHRP, I1 - ISIS L1, I2 - ISIS L2, IA - ISIS interarea IS - ISIS summary, D - EIGRP, EX - EIGRP external, NM - NEMO ND - ND Default, NDp - ND Prefix, DCE - Destination, NDr - Redirect O - OSPF Intra, OI - OSPF Inter, OE1 - OSPF ext 1, OE2 - OSPF ext 2 ON1 - OSPF NSSA ext 1, ON2 - OSPF NSSA ext 2, l - LISP I1 ::/0 [115/10] via FE80::C803:19FF:FE84:8, FastEthernet0/0 IA 2001:10:1:24::/64 [115/40] via FE80::C803:19FF:FE84:8, FastEthernet0/0 IA 2001:10:1:25::/64 [115/40] via FE80::C803:19FF:FE84:8, FastEthernet0/0 IA 2001:10:1:34::/64 [115/30] via FE80::C803:19FF:FE84:8, FastEthernet0/0 I1 2001:10:1:38::/64 [115/20] via FE80::C803:19FF:FE84:8, FastEthernet0/0 IA 2001:10:1:46::/64 [115/40] via FE80::C803:19FF:FE84:8, FastEthernet0/0 IA 2001:10:1:56::/64 [115/50] via FE80::C803:19FF:FE84:8, FastEthernet0/0 IA 2001:10:1:57::/64 [115/50] via FE80::C803:19FF:FE84:8, FastEthernet0/0 IA 2001:10:1:67::/64 [115/50] via FE80::C803:19FF:FE84:8, FastEthernet0/0 C 2001:10:1:89::/64 [0/0] via FastEthernet0/0, directly connected L 2001:10:1:89::9/128 [0/0] via FastEthernet0/0, receive IA 2001:10:1:123::/64 [115/30] via FE80::C803:19FF:FE84:8, FastEthernet0/0 IA 2001:172:16::/48 [115/30] via FE80::C803:19FF:FE84:8, FastEthernet0/0 IA 2001:192:168:1::1/128 [115/30] via FE80::C803:19FF:FE84:8, FastEthernet0/0 IA 2001:192:168:1::2/128 [115/30] via FE80::C803:19FF:FE84:8, FastEthernet0/0 IA 2001:192:168:1::3/128 [115/20] via FE80::C803:19FF:FE84:8, FastEthernet0/0 IA 2001:192:168:1::4/128 [115/30] via FE80::C803:19FF:FE84:8, FastEthernet0/0 IA 2001:192:168:1::5/128 [115/40] via FE80::C803:19FF:FE84:8, FastEthernet0/0 IA 2001:192:168:1::6/128 [115/40] via FE80::C803:19FF:FE84:8, FastEthernet0/0 IA 2001:192:168:1::7/128 [115/50] via FE80::C803:19FF:FE84:8, FastEthernet0/0 I1 2001:192:168:1::8/128 [115/10] via FE80::C803:19FF:FE84:8, FastEthernet0/0 LC 2001:192:168:1::9/128 [0/0] via Loopback0, receive IA 2001:192:168:1::10/128 [115/30] via FE80::C803:19FF:FE84:8, FastEthernet0/0 L FF00::/8 [0/0] via Null0, receive R10#show ipv6 route IPv6 Routing Table - default - 29 entries Codes: C - Connected, L - Local, S - Static, U - Per-user Static route B - BGP, HA - Home Agent, MR - Mobile Router, R - RIP H - NHRP, I1 - ISIS L1, I2 - ISIS L2, IA - ISIS interarea IS - ISIS summary, D - EIGRP, EX - EIGRP external, NM - NEMO ND - ND Default, NDp - ND Prefix, DCE - Destination, NDr - Redirect O - OSPF Intra, OI - OSPF Inter, OE1 - OSPF ext 1, OE2 - OSPF ext 2 ON1 - OSPF NSSA ext 1, ON2 - OSPF NSSA ext 2, l - LISP OE2 2001:10:1:24::/64 [110/20] via FE80::C804:30FF:FE9C:6, FastEthernet0/1 OE2 2001:10:1:25::/64 [110/20] via FE80::C804:30FF:FE9C:6, FastEthernet0/1 OE2 2001:10:1:34::/64 [110/20] via FE80::C804:30FF:FE9C:6, FastEthernet0/1 OE2 2001:10:1:38::/64 [110/20] via FE80::C804:30FF:FE9C:6, FastEthernet0/1 OE2 2001:10:1:46::/64 [110/20] via FE80::C804:30FF:FE9C:6, FastEthernet0/1 OE2 2001:10:1:56::/64 [110/20] via FE80::C804:30FF:FE9C:6, FastEthernet0/1 OE2 2001:10:1:57::/64 [110/20] via FE80::C804:30FF:FE9C:6, FastEthernet0/1 OE2 2001:10:1:67::/64 [110/20] via FE80::C804:30FF:FE9C:6, FastEthernet0/1 OE2 2001:10:1:89::/64 [110/20] via FE80::C804:30FF:FE9C:6, FastEthernet0/1 C 2001:172:16::/64 [0/0] via Loopback1, directly connected L 2001:172:16::1/128 [0/0] via Loopback1, receive C 2001:172:16:1::/64 [0/0] via Loopback2, directly connected L 2001:172:16:1::1/128 [0/0] via Loopback2, receive C 2001:172:16:2::/64 [0/0] via Loopback3, directly connected L 2001:172:16:2::1/128 [0/0] via Loopback3, receive C 2001:172:16:3::/64 [0/0] via Loopback4, directly connected L 2001:172:16:3::1/128 [0/0] via Loopback4, receive C 2001:172:16:110::/64 [0/0] via FastEthernet0/1, directly connected L 2001:172:16:110::10/128 [0/0] via FastEthernet0/1, receive OE2 2001:192:168:1::2/128 [110/20] via FE80::C804:30FF:FE9C:6, FastEthernet0/1 OE2 2001:192:168:1::3/128 [110/20] via FE80::C804:30FF:FE9C:6, FastEthernet0/1 OE2 2001:192:168:1::4/128 [110/20] via FE80::C804:30FF:FE9C:6, FastEthernet0/1 OE2 2001:192:168:1::5/128 [110/20] via FE80::C804:30FF:FE9C:6, FastEthernet0/1 OE2 2001:192:168:1::6/128 [110/20] via FE80::C804:30FF:FE9C:6, FastEthernet0/1 OE2 2001:192:168:1::7/128 [110/20] via FE80::C804:30FF:FE9C:6, FastEthernet0/1 OE2 2001:192:168:1::8/128 [110/20] via FE80::C804:30FF:FE9C:6, FastEthernet0/1 OE2 2001:192:168:1::9/128 [110/20] via FE80::C804:30FF:FE9C:6, FastEthernet0/1 LC 2001:192:168:1::10/128 [0/0] via Loopback0, receive L FF00::/8 [0/0] via Null0, receive
Ping and Traceroute
!!-- Ping R10 network from R7 --!! R7#ping 2001:172:16:1::1 source loopback 0 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 2001:172:16:1::1, timeout is 2 seconds: Packet sent with a source address of 2001:192:168:1::7 !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 124/132/144 ms !!-- Traceroute R10 network from R7 --!! R7#traceroute ipv6 Target IPv6 address: 2001:172:16:1::1 Source address: 2001:192:168:1::7 Insert source routing header? [no]: Numeric display? [no]: Timeout in seconds [3]: Probe count [3]: Minimum Time to Live [1]: Maximum Time to Live [30]: Priority [0]: Port Number [0]: Type escape sequence to abort. Tracing the route to 2001:172:16:1::1 1 2001:10:1:57::5 64 msec 48 msec 36 msec 2 2001:10:1:25::2 76 msec 76 msec 60 msec 3 2001:10:1:123::1 108 msec 108 msec 92 msec 4 2001:172:16:110::10 164 msec 144 msec 144 msec !!-- Ping R9 from R7 --!! R7#ping 2001:192:168:1::9 source loopback 0 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 2001:192:168:1::9, timeout is 2 seconds: Packet sent with a source address of 2001:192:168:1::7 !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 140/164/188 ms !!-- Traceroute R9 from R7 --!! R7#traceroute ipv6 Target IPv6 address: 2001:192:168:1::9 Source address: 2001:192:168:1::7 Insert source routing header? [no]: Numeric display? [no]: Timeout in seconds [3]: Probe count [3]: Minimum Time to Live [1]: Maximum Time to Live [30]: Priority [0]: Port Number [0]: Type escape sequence to abort. Tracing the route to 2001:192:168:1::9 1 2001:10:1:57::5 76 msec 48 msec 36 msec 2 2001:10:1:25::2 76 msec 64 msec 76 msec 3 2001:10:1:123::3 124 msec 148 msec 108 msec 4 2001:10:1:38::8 152 msec 148 msec 152 msec 5 2001:10:1:89::9 176 msec 196 msec 156 msec !!-- Ping R10 network from R9 --!! R9#ping 2001:172:16:1::1 source loopback 0 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 2001:172:16:1::1, timeout is 2 seconds: Packet sent with a source address of 2001:192:168:1::9 !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 128/139/152 ms !!-- Traceroute R10 network from R9 --!! R9#traceroute ipv6 Target IPv6 address: 2001:172:16:1::1 Source address: 2001:192:168:1::9 Insert source routing header? [no]: Numeric display? [no]: Timeout in seconds [3]: Probe count [3]: Minimum Time to Live [1]: Maximum Time to Live [30]: Priority [0]: Port Number [0]: Type escape sequence to abort. Tracing the route to 2001:172:16:1::1 1 2001:10:1:89::8 84 msec 52 msec 32 msec 2 2001:10:1:38::3 104 msec 76 msec 84 msec 3 2001:10:1:123::1 132 msec 112 msec 112 msec 4 2001:172:16:110::10 160 msec 164 msec 120 msec
Currently, we are using single IS-IS topology, entire network is dual stacked and using the same database structure for IPv4 and IPv6 routing.
!! -- We have configured different metric for IPv4 and IPv6 -- !! !! -- As we are using the IS-IS Single Topology, which is using --!! !! -- same database structure for both IPv4 and IPv6 routing --!! !! -- We have increased IS-IS metric for IPv4 on interface Fa0/1 -- !! !! -- to make low cost path via Fa0/0 -- !! !! -- We have increased IS-IS metric for IPv6 on interface Fa0/0 -- !! !! -- to make low cost path via Fa0/1 -- !! !! -- But because of IS-IS single topology for both IPv4 and IPv6 --!! !! -- Fa0/0 becomes low cost/preferred path for both IPv4 and IPv6-!! R7# interface FastEthernet0/0 ip address 10.1.57.7 255.255.255.0 ip router isis 1 duplex full speed 100 ipv6 address 2001:10:1:57::7/64 ipv6 router isis 1 isis network point-to-point isis ipv6 metric 20 ! interface FastEthernet0/1 ip address 10.1.67.7 255.255.255.0 ip router isis 1 duplex full speed 100 ipv6 address 2001:10:1:67::7/64 ipv6 router isis 1 isis metric 20 R7#sh isis database detail <snip> R7.00-00 * 0x00000003 0xB5AC 894 0/0/0 Area Address: 49.0002 NLPID: 0xCC 0x8E Hostname: R7 IP Address: 192.168.1.7 Metric: 10 IP 10.1.57.0 255.255.255.0 Metric: 20 IP 10.1.67.0 255.255.255.0 Metric: 0 IP 192.168.1.7 255.255.255.255 IPv6 Address: 2001:192:168:1::7 Metric: 10 IPv6 2001:10:1:57::/64 Metric: 20 IPv6 2001:10:1:67::/64 Metric: 0 IPv6 2001:192:168:1::7/128 Metric: 20 IS R7.01 Metric: 10 IS R5.00 R7.01-00 * 0x00000002 0xD753 841 0/0/0 Metric: 0 IS R7.00 Metric: 0 IS R6.00 R7# show ip route 0.0.0.0 Routing entry for 0.0.0.0/0, supernet Known via "isis", distance 115, metric 10, candidate default path, type level-1 Redistributing via isis 1 Last update from 10.1.57.5 on FastEthernet0/0, 00:21:21 ago Routing Descriptor Blocks: * 10.1.57.5, from 192.168.1.5, 00:21:21 ago, via FastEthernet0/0 Route metric is 10, traffic share count is 1 R7#show ipv6 route ::/0 Routing entry for ::/0 Known via "isis 1", distance 115, metric 10, type level-1 Route count is 1/1, share count 0 Routing paths: FE80::C800:11FF:FEB0:8, FastEthernet0/0 Last updated 00:21:36 ago
We need to configure IS-IS Multi Topology to create different routing topologies for IPv4 and IPv6 address family. Wide metric is also required for Multi topology configuration.
ISIS Multi Topology Configuration
R1 hostname R1 ! no ip domain lookup ip cef ipv6 unicast-routing ipv6 cef ! interface Loopback0 ip address 192.168.1.1 255.255.255.255 ipv6 address 2001:192:168:1::1/128 ! interface FastEthernet0/0 ip address 10.1.123.1 255.255.255.0 ip router isis 1 ipv6 address 2001:10:1:123::1/64 ipv6 router isis 1 ! interface FastEthernet0/1 ip address 172.16.110.1 255.255.255.0 ipv6 address 2001:172:16:110::1/64 ipv6 ospf 100 area 0 ! router ospf 1 redistribute isis 1 level-1-2 subnets passive-interface default no passive-interface FastEthernet0/1 network 172.16.110.1 0.0.0.0 area 0 network 192.168.1.1 0.0.0.0 area 0 ! router isis 1 net 49.0001.1921.6800.1001.00 is-type level-2-only metric-style wide redistribute ospf 1 match internal external 1 external 2 passive-interface Loopback0 ! address-family ipv6 multi-topology redistribute ospf 100 match internal external 1 external 2 exit-address-family ! ipv6 router ospf 100 redistribute isis 1 level-1-2 ! R2 hostname R2 ! no ip domain lookup ip cef ipv6 unicast-routing ipv6 cef ! interface Loopback0 ip address 192.168.1.2 255.255.255.255 ipv6 address 2001:192:168:1::2/128 ! interface FastEthernet0/0 ip address 10.1.123.2 255.255.255.0 ip router isis 1 ipv6 address 2001:10:1:123::2/64 ipv6 router isis 1 ! interface FastEthernet0/1 ip address 10.1.25.2 255.255.255.0 ip router isis 1 ipv6 address 2001:10:1:25::2/64 ipv6 router isis 1 ! interface FastEthernet1/0 ip address 10.1.24.2 255.255.255.0 ip router isis 1 ipv6 address 2001:10:1:24::2/64 ipv6 router isis 1 ! router isis 1 net 49.0001.1921.6800.1002.00 is-type level-2-only metric-style wide passive-interface Loopback0 ! address-family ipv6 multi-topology exit-address-family ! R3 hostname R3 ! no ip domain lookup ip cef ipv6 unicast-routing ipv6 cef ! interface Loopback0 ip address 192.168.1.3 255.255.255.255 ipv6 address 2001:192:168:1::3/128 ! interface FastEthernet0/0 ip address 10.1.123.3 255.255.255.0 ip router isis 1 ipv6 address 2001:10:1:123::3/64 ipv6 router isis 1 ! interface FastEthernet0/1 ip address 10.1.38.3 255.255.255.0 ip router isis 1 ipv6 address 2001:10:1:38::3/64 ipv6 router isis 1 ! interface FastEthernet1/0 ip address 10.1.34.3 255.255.255.0 ip router isis 1 ipv6 address 2001:10:1:34::3/64 ipv6 router isis 1 ! router isis 1 net 49.0001.1921.6800.1003.00 is-type level-2-only metric-style wide passive-interface Loopback0 ! address-family ipv6 multi-topology exit-address-family ! R4 hostname R4 ! no ip domain lookup ip cef ipv6 unicast-routing ipv6 cef ! interface Loopback0 ip address 192.168.1.4 255.255.255.255 ipv6 address 2001:192:168:1::4/128 ! interface FastEthernet0/0 ip address 10.1.34.4 255.255.255.0 ip router isis 1 ipv6 address 2001:10:1:34::4/64 ipv6 router isis 1 isis circuit-type level-2-only ! interface FastEthernet0/1 ip address 10.1.46.4 255.255.255.0 ip router isis 1 ipv6 address 2001:10:1:46::4/64 ipv6 router isis 1 isis circuit-type level-2-only ! interface FastEthernet1/0 ip address 10.1.24.4 255.255.255.0 ip router isis 1 ipv6 address 2001:10:1:24::4/64 ipv6 router isis 1 isis circuit-type level-2-only ! router isis 1 net 49.0001.1921.6800.1004.00 metric-style wide passive-interface Loopback0 ! address-family ipv6 multi-topology exit-address-family ! R5 hostname R5 ! no ip domain lookup ip cef ipv6 unicast-routing ipv6 cef ! interface Loopback0 ip address 192.168.1.5 255.255.255.255 ipv6 address 2001:192:168:1::5/128 ! interface FastEthernet0/0 ip address 10.1.57.5 255.255.255.0 ip router isis 1 ipv6 address 2001:10:1:57::5/64 ipv6 router isis 1 isis network point-to-point ! interface FastEthernet0/1 ip address 10.1.25.5 255.255.255.0 ip router isis 1 ipv6 address 2001:10:1:25::5/64 ipv6 router isis 1 ! interface FastEthernet1/0 ip address 10.1.56.5 255.255.255.0 ip router isis 1 ipv6 address 2001:10:1:56::5/64 ipv6 router isis 1 ! router isis 1 net 49.0002.1921.6800.1005.00 metric-style wide passive-interface Loopback0 ! address-family ipv6 multi-topology exit-address-family ! R6 hostname R6 ! no ip domain lookup ip cef ipv6 unicast-routing ipv6 cef ! interface Loopback0 ip address 192.168.1.6 255.255.255.255 ipv6 address 2001:192:168:1::6/128 ! interface FastEthernet0/0 ip address 10.1.67.6 255.255.255.0 ip router isis 1 ipv6 address 2001:10:1:67::6/64 ipv6 router isis 1 ! interface FastEthernet0/1 ip address 10.1.46.6 255.255.255.0 ip router isis 1 ipv6 address 2001:10:1:46::6/64 ipv6 router isis 1 ! interface FastEthernet1/0 ip address 10.1.56.6 255.255.255.0 ip router isis 1 ipv6 address 2001:10:1:56::6/64 ipv6 router isis 1 ! router isis 1 net 49.0002.1921.6800.1006.00 metric-style wide passive-interface Loopback0 ! address-family ipv6 multi-topology exit-address-family ! R7 hostname R7 ! no ip domain lookup ip cef ipv6 unicast-routing ipv6 cef ! interface Loopback0 ip address 192.168.1.7 255.255.255.255 ipv6 address 2001:192:168:1::7/128 ! interface FastEthernet0/0 ip address 10.1.57.7 255.255.255.0 ip router isis 1 ipv6 address 2001:10:1:57::7/64 ipv6 router isis 1 isis network point-to-point isis ipv6 metric 20 ! interface FastEthernet0/1 ip address 10.1.67.7 255.255.255.0 ip router isis 1 ipv6 address 2001:10:1:67::7/64 ipv6 router isis 1 isis metric 20 ! router isis 1 net 49.0002.1921.6800.1007.00 is-type level-1 metric-style wide passive-interface Loopback0 ! address-family ipv6 multi-topology exit-address-family ! R8 hostname R8 ! no ip domain lookup ip cef ipv6 unicast-routing ipv6 cef ! interface Loopback0 ip address 192.168.1.8 255.255.255.255 ipv6 address 2001:192:168:1::8/128 ! interface FastEthernet0/0 ip address 10.1.89.8 255.255.255.0 ip router isis 1 ipv6 address 2001:10:1:89::8/64 ipv6 router isis 1 ! interface FastEthernet0/1 ip address 10.1.38.8 255.255.255.0 ip router isis 1 ipv6 address 2001:10:1:38::8/64 ipv6 router isis 1 ! router isis 1 net 49.0003.1921.6800.1008.00 metric-style wide summary-address 172.16.0.0 255.255.252.0 level-1 redistribute isis ip level-2 into level-1 distribute-list 100 passive-interface Loopback0 ! address-family ipv6 multi-topology summary-prefix 2001:172:16::/48 level-1 redistribute isis level-2 into level-1 distribute-list IPv6_L2_PREFIXES exit-address-family ! access-list 100 permit ip any any ! ipv6 prefix-list IPv6_L2_PREFIXES seq 5 permit ::/0 le 128 ! R9 hostname R9 ! no ip domain lookup ip cef ipv6 unicast-routing ipv6 cef ! interface Loopback0 ip address 192.168.1.9 255.255.255.255 ipv6 address 2001:192:168:1::9/128 ! interface FastEthernet0/0 ip address 10.1.89.9 255.255.255.0 ip router isis 1 ipv6 address 2001:10:1:89::9/64 ipv6 router isis 1 ! router isis 1 net 49.0003.1921.6800.1009.00 is-type level-1 metric-style wide passive-interface Loopback0 ! address-family ipv6 multi-topology exit-address-family ! R10 hostname R10 ! no ip domain lookup ip cef ipv6 unicast-routing ipv6 cef ! interface Loopback0 ip address 192.168.1.10 255.255.255.255 ipv6 address 2001:192:168:1::10/128 ipv6 ospf 100 area 0 ! interface Loopback1 ip address 172.16.0.1 255.255.255.0 ip ospf network point-to-point ipv6 address 2001:172:16::1/64 ipv6 ospf 100 area 0 ipv6 ospf network point-to-point ! interface Loopback2 ip address 172.16.1.1 255.255.255.0 ip ospf network point-to-point ipv6 address 2001:172:16:1::1/64 ipv6 ospf 100 area 0 ipv6 ospf network point-to-point ! interface Loopback3 ip address 172.16.2.1 255.255.255.0 ip ospf network point-to-point ipv6 address 2001:172:16:2::1/64 ipv6 ospf 100 area 0 ipv6 ospf network point-to-point ! interface Loopback4 ip address 172.16.3.1 255.255.255.0 ip ospf network point-to-point ipv6 address 2001:172:16:3::1/64 ipv6 ospf 100 area 0 ipv6 ospf network point-to-point ! interface FastEthernet0/1 ip address 172.16.110.10 255.255.255.0 ipv6 address 2001:172:16:110::10/64 ipv6 ospf 100 area 0 ! router ospf 1 network 0.0.0.0 255.255.255.255 area 0 ! ipv6 router ospf 100 !
Verification and Testing
!! -- Below output shows that wide metric is used now -- !! R7#show clns protocol IS-IS Router: 1 System Id: 1921.6800.1007.00 IS-Type: level-1 Manual area address(es): 49.0002 Routing for area address(es): 49.0002 Interfaces supported by IS-IS: FastEthernet0/1 - IP - IPv6 FastEthernet0/0 - IP - IPv6 Passive interface: Loopback0 Redistribute: static (on by default) Distance for L2 CLNS routes: 110 RRR level: none Generate narrow metrics: none Accept narrow metrics: none Generate wide metrics: level-1-2 Accept wide metrics: level-1-2 !! -- MT-IPv6 shows that Multi Topology is in use now -- !! !! -- Which is different topology for IPv4 and IPv6 -- !! R7#show isis database detail Tag 1: IS-IS Level-1 Link State Database: LSPID LSP Seq Num LSP Checksum LSP Holdtime ATT/P/OL R5.00-00 0x00000003 0xB859 936 1/0/0 Area Address: 49.0002 Topology: IPv4 (0x0) IPv6 (0x4002 ATT) NLPID: 0xCC 0x8E Hostname: R5 IP Address: 192.168.1.5 Metric: 10 IP 10.1.57.0/24 Metric: 10 IP 10.1.25.0/24 Metric: 10 IP 10.1.56.0/24 Metric: 0 IP 192.168.1.5/32 IPv6 Address: 2001:192:168:1::5 Metric: 10 IPv6 (MT-IPv6) 2001:10:1:57::/64 Metric: 10 IPv6 (MT-IPv6) 2001:10:1:25::/64 Metric: 10 IPv6 (MT-IPv6) 2001:10:1:56::/64 Metric: 0 IPv6 (MT-IPv6) 2001:192:168:1::5/128 Metric: 10 IS-Extended R6.03 Metric: 10 IS-Extended R7.00 Metric: 10 IS (MT-IPv6) R6.03 Metric: 10 IS (MT-IPv6) R7.00 R6.00-00 0x00000005 0x387F 943 1/0/0 Area Address: 49.0002 Topology: IPv4 (0x0) IPv6 (0x4002 ATT) NLPID: 0xCC 0x8E Hostname: R6 IP Address: 192.168.1.6 Metric: 10 IP 10.1.67.0/24 Metric: 10 IP 10.1.46.0/24 Metric: 10 IP 10.1.56.0/24 Metric: 0 IP 192.168.1.6/32 IPv6 Address: 2001:192:168:1::6 Metric: 10 IPv6 (MT-IPv6) 2001:10:1:67::/64 Metric: 10 IPv6 (MT-IPv6) 2001:10:1:46::/64 Metric: 10 IPv6 (MT-IPv6) 2001:10:1:56::/64 Metric: 0 IPv6 (MT-IPv6) 2001:192:168:1::6/128 Metric: 10 IS-Extended R6.03 Metric: 10 IS-Extended R7.01 Metric: 10 IS (MT-IPv6) R6.03 Metric: 10 IS (MT-IPv6) R7.01 R6.03-00 0x00000001 0x73A7 929 0/0/0 Metric: 0 IS-Extended R6.00 Metric: 0 IS-Extended R5.00 R7.00-00 * 0x00000003 0x66A9 930 0/0/0 Area Address: 49.0002 Topology: IPv4 (0x0) IPv6 (0x2) NLPID: 0xCC 0x8E Hostname: R7 IP Address: 192.168.1.7 Metric: 10 IP 10.1.57.0/24 Metric: 20 IP 10.1.67.0/24 Metric: 0 IP 192.168.1.7/32 IPv6 Address: 2001:192:168:1::7 Metric: 20 IPv6 (MT-IPv6) 2001:10:1:57::/64 Metric: 10 IPv6 (MT-IPv6) 2001:10:1:67::/64 Metric: 0 IPv6 (MT-IPv6) 2001:192:168:1::7/128 Metric: 20 IS-Extended R7.01 Metric: 10 IS-Extended R5.00 Metric: 10 IS (MT-IPv6) R7.01 Metric: 20 IS (MT-IPv6) R5.00 R7.01-00 * 0x00000001 0x9487 927 0/0/0 Metric: 0 IS-Extended R7.00 Metric: 0 IS-Extended R6.00
Ping and Traceroute
!! -- Now IPv4 routing is preferred via Fa0/0 -- !! !! -- And IPv6 routing is preferred via Fa0/1 -- !! R7#show ip route Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2 E1 - OSPF external type 1, E2 - OSPF external type 2 i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2 ia - IS-IS inter area, * - candidate default, U - per-user static route o - ODR, P - periodic downloaded static route, H - NHRP, l - LISP + - replicated route, % - next hop override Gateway of last resort is 10.1.57.5 to network 0.0.0.0 i*L1 0.0.0.0/0 [115/10] via 10.1.57.5, 00:08:09, FastEthernet0/0 10.0.0.0/8 is variably subnetted, 7 subnets, 2 masks i L1 10.1.25.0/24 [115/20] via 10.1.57.5, 00:08:19, FastEthernet0/0 i L1 10.1.46.0/24 [115/30] via 10.1.67.6, 00:08:19, FastEthernet0/1 [115/30] via 10.1.57.5, 00:08:19, FastEthernet0/0 i L1 10.1.56.0/24 [115/20] via 10.1.57.5, 00:08:19, FastEthernet0/0 C 10.1.57.0/24 is directly connected, FastEthernet0/0 L 10.1.57.7/32 is directly connected, FastEthernet0/0 C 10.1.67.0/24 is directly connected, FastEthernet0/1 L 10.1.67.7/32 is directly connected, FastEthernet0/1 192.168.1.0/32 is subnetted, 3 subnets i L1 192.168.1.5 [115/10] via 10.1.57.5, 00:08:19, FastEthernet0/0 i L1 192.168.1.6 [115/20] via 10.1.67.6, 00:08:19, FastEthernet0/1 [115/20] via 10.1.57.5, 00:08:19, FastEthernet0/0 C 192.168.1.7 is directly connected, Loopback0 R7#show ipv6 route IPv6 Routing Table - default - 12 entries Codes: C - Connected, L - Local, S - Static, U - Per-user Static route B - BGP, HA - Home Agent, MR - Mobile Router, R - RIP H - NHRP, I1 - ISIS L1, I2 - ISIS L2, IA - ISIS interarea IS - ISIS summary, D - EIGRP, EX - EIGRP external, NM - NEMO ND - ND Default, NDp - ND Prefix, DCE - Destination, NDr - Redirect O - OSPF Intra, OI - OSPF Inter, OE1 - OSPF ext 1, OE2 - OSPF ext 2 ON1 - OSPF NSSA ext 1, ON2 - OSPF NSSA ext 2, l - LISP I1 ::/0 [115/10] via FE80::C801:11FF:FEB0:8, FastEthernet0/1 I1 2001:10:1:25::/64 [115/30] via FE80::C800:11FF:FEB0:8, FastEthernet0/0 via FE80::C801:11FF:FEB0:8, FastEthernet0/1 I1 2001:10:1:46::/64 [115/20] via FE80::C801:11FF:FEB0:8, FastEthernet0/1 I1 2001:10:1:56::/64 [115/20] via FE80::C801:11FF:FEB0:8, FastEthernet0/1 C 2001:10:1:57::/64 [0/0] via FastEthernet0/0, directly connected L 2001:10:1:57::7/128 [0/0] via FastEthernet0/0, receive C 2001:10:1:67::/64 [0/0] via FastEthernet0/1, directly connected L 2001:10:1:67::7/128 [0/0] via FastEthernet0/1, receive I1 2001:192:168:1::5/128 [115/20] via FE80::C800:11FF:FEB0:8, FastEthernet0/0 via FE80::C801:11FF:FEB0:8, FastEthernet0/1 I1 2001:192:168:1::6/128 [115/10] via FE80::C801:11FF:FEB0:8, FastEthernet0/1 LC 2001:192:168:1::7/128 [0/0] via Loopback0, receive L FF00::/8 [0/0] via Null0, receive R7# interface FastEthernet0/0 ip address 10.1.57.7 255.255.255.0 ip router isis 1 duplex full speed 100 ipv6 address 2001:10:1:57::7/64 ipv6 router isis 1 isis network point-to-point isis ipv6 metric 20 ! interface FastEthernet0/1 ip address 10.1.67.7 255.255.255.0 ip router isis 1 duplex full speed 100 ipv6 address 2001:10:1:67::7/64 ipv6 router isis 1 isis metric 20 ! R7#show ip route 0.0.0.0 Routing entry for 0.0.0.0/0, supernet Known via "isis", distance 115, metric 10, candidate default path, type level-1 Redistributing via isis 1 Last update from 10.1.57.5 on FastEthernet0/0, 00:09:02 ago Routing Descriptor Blocks: * 10.1.57.5, from 192.168.1.5, 00:09:02 ago, via FastEthernet0/0 Route metric is 10, traffic share count is 1 R7#show ipv6 route ::/0 Routing entry for ::/0 Known via "isis 1", distance 115, metric 10, type level-1 Route count is 1/1, share count 0 Routing paths: FE80::C801:11FF:FEB0:8, FastEthernet0/1 Last updated 00:09:08 ago !!-- Ping R10 IPv4 network from R7 --!! R7#ping 172.16.1.1 source loopback 0 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 172.16.1.1, timeout is 2 seconds: Packet sent with a source address of 192.168.1.7 !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 96/106/116 ms !!-- Traceroute R10 IPv4 network from R7 --!! R7#traceroute 172.16.1.1 source loopback 0 Type escape sequence to abort. Tracing the route to 172.16.1.1 VRF info: (vrf in name/id, vrf out name/id) 1 10.1.57.5 40 msec 48 msec 56 msec 2 10.1.25.2 56 msec 56 msec 44 msec 3 10.1.123.1 84 msec 76 msec 96 msec 4 172.16.110.10 100 msec * 104 msec !!-- Ping R10 IPv6 network from R7 --!! R7#ping 2001:172:16::1 source loopback 0 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 2001:172:16::1, timeout is 2 seconds: Packet sent with a source address of 2001:192:168:1::7 !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 80/100/124 ms !!-- Traceroute R10 IPv6 network from R7 --!! R7#traceroute ipv6 Target IPv6 address: 2001:172:16::1 Source address: 2001:192:168:1::7 Insert source routing header? [no]: Numeric display? [no]: Timeout in seconds [3]: Probe count [3]: Minimum Time to Live [1]: Maximum Time to Live [30]: Priority [0]: Port Number [0]: Type escape sequence to abort. Tracing the route to 2001:172:16::1 1 2001:10:1:67::6 88 msec 52 msec 24 msec 2 2001:10:1:56::5 40 msec 40 msec 48 msec 3 2001:10:1:25::2 72 msec 60 msec 76 msec 4 2001:10:1:123::1 96 msec 96 msec 92 msec 5 2001:172:16:110::10 104 msec 120 msec 104 msec