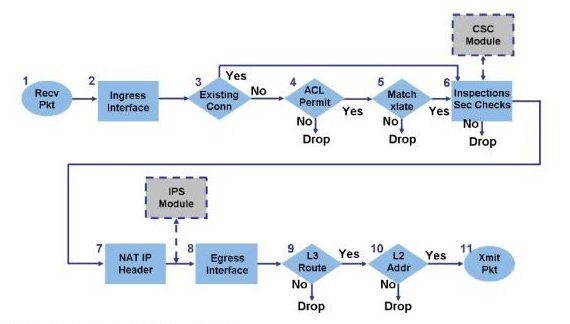
I have configured JunOS in GNS3. You can refer below link to simulate a JunOS device with GNS3.
http://muralirajanm.blogspot.in/2011/01/gns3.html
We will discuss these topics in this post:
1. First time login to JunOS device
2. User Account
3. Interface IP address configuration
4. Static Routing in JunOS
5. Floating Static route – Qualified-next-hop
We will use this topology.
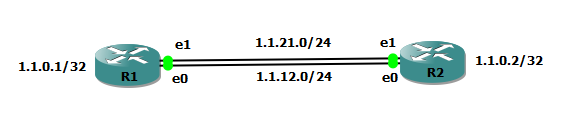
When you log in to a JunOS device, you are placed into one of two shells:
– C shell %
– CLI in operational mode user@router> (operational mode)
user@router# (configuration mode)
The root account or user is a predefined user name in JunOS. The root user is by default the administrator or super user, who has absolute permission to both configure and install software on a device. JunOS requires configuration of the root password before it accepts a commit. On a new device the root password must always be a part of the configuration submitted with your initial commit.
There is no default password for root account in initial configuration. You just need to type username as root and hit enter. When you login with root account, you will be placed in ‘C shell’. You have to type ‘cli’ to go to operational mode.
login: root
— JUNOS 10.1R1.8 built 2010-02-12 17:15:05 UTC
root@%
root@%
root@%
root@%
root@% cli
root>
Let’s configure hostname of device.
Type ‘configure’ in cli mode. It will change the prompt and place you in edit configuration mode.
root> configure
Entering configuration mode
[edit]
root#
[edit]
root# set system host-name R1
JunOS device does not use any of this configuration until you issue a commit command.
root# commit
[edit]
‘system’
Missing mandatory statement: ‘root-authentication’
error: commit failed: (missing statements)
[edit]
root#
Commit configuration is failed because root account must have a password before committing any configuration.
Let’s configure password for root account.
root# set system root-authentication plain-text-password
New password: *********
Retype new password: *********
[edit]
root# commit
commit complete
Let’s create other local user account. Class super-user is equivalent to privilege level 15 in Cisco IOS.
root@R1# set system login user amolak authentication plain-text-password
New password:
Retype new password:
[edit]
root@R1# set system login user amolak class super-user
[edit]
root@R1# commit
commit complete
[edit]
root@R1# exit
Exiting configuration mode
root@R1> exit
root@% exit
logout
R1 (ttyd0)
login: amolak
Password:
— JUNOS 10.1R1.8 built 2010-02-12 17:15:05 UTC
amolak@R1>
Now we will configure IP address on interface as per our topology.
– Each and every interface within the JunOS software requires at least one logical interface, called a unit. This is where all addressing and protocol information is configured.
– The inet protocol family supports IP version 4 (IPv4) packets.
amolak@R1# set interfaces em0 unit 0 family inet address 1.1.12.1/24
[edit]
amolak@R1# set interfaces em1 unit 0 family inet address 1.1.21.1/24
[edit]
amolak@R1# set interfaces lo0 unit 0 family inet address 1.1.0.1/32
[edit]
amolak@R1# commit
commit complete
[edit]
amolak@R1#
Similarly, configure R2.
amolak@R2> configure
Entering configuration mode
[edit]
amolak@R2# set interfaces em0 unit 0 family inet address 1.1.12.2/24
[edit]
amolak@R2# set interfaces em1 unit 0 family inet address 1.1.21.2/24
[edit]
amolak@R2# set interfaces lo0 unit 0 family inet address 1.1.0.2/32
[edit]
amolak@R2# commit
commit complete
[edit]
amolak@R2#
Lets verify the IP address on interfaces with show command. I have filtered interfaces only having IPv4 (family inet) address configured with “| match inet’.
amolak@R1> show interfaces terse | match inet
em0.0 up up inet 1.1.12.1/24
em1.0 up up inet 1.1.21.1/24
lo0.0 up up inet 1.1.0.1 –> 0/0
amolak@R2# run show interfaces terse | match inet
em0.0 up up inet 1.1.12.2/24
em1.0 up up inet 1.1.21.2/24
lo0.0 up up inet 1.1.0.2 –> 0/0
Verify the PING reachability.
amolak@R1> ping 1.1.12.2
PING 1.1.12.2 (1.1.12.2): 56 data bytes
64 bytes from 1.1.12.2: icmp_seq=0 ttl=64 time=23.090 ms
64 bytes from 1.1.12.2: icmp_seq=1 ttl=64 time=1.026 ms
^C
— 1.1.12.2 ping statistics —
2 packets transmitted, 2 packets received, 0% packet loss
round-trip min/avg/max/stddev = 1.026/12.058/23.090/11.032 ms
amolak@R1> ping 1.1.21.2
PING 1.1.21.2 (1.1.21.2): 56 data bytes
64 bytes from 1.1.21.2: icmp_seq=0 ttl=64 time=2.109 ms
64 bytes from 1.1.21.2: icmp_seq=1 ttl=64 time=0.719 ms
^C
— 1.1.21.2 ping statistics —
2 packets transmitted, 2 packets received, 0% packet loss
round-trip min/avg/max/stddev = 0.719/1.414/2.109/0.695 ms
Create a static route to reach Loopback interface IP address.
amolak@R1# set routing-options static route 1.1.0.2/32 next-hop 1.1.12.2
[edit]
amolak@R1# commit
commit complete
amolak@R2# set routing-options static route 1.1.0.1/32 next-hop 1.1.12.1
[edit]
amolak@R2# commit
commit complete
amolak@R1# exit
Exiting configuration mode
Verify PING to loopback interface IP.
amolak@R1> ping 1.1.0.2 source 1.1.0.1
PING 1.1.0.2 (1.1.0.2): 56 data bytes
64 bytes from 1.1.0.2: icmp_seq=0 ttl=64 time=0.650 ms
64 bytes from 1.1.0.2: icmp_seq=1 ttl=64 time=0.964 ms
64 bytes from 1.1.0.2: icmp_seq=2 ttl=64 time=0.780 ms
^C
— 1.1.0.2 ping statistics —
3 packets transmitted, 3 packets received, 0% packet loss
round-trip min/avg/max/stddev = 0.650/0.798/0.964/0.129 ms
amolak@R1>
amolak@R1> show route 1.1.0.2
inet.0: 6 destinations, 6 routes (6 active, 0 holddown, 0 hidden)
+ = Active Route, – = Last Active, * = Both
1.1.0.2/32 *[Static/5] 00:01:05
> to 1.1.12.2 via em0.0
By default, the static route has a default preference value of five. In general, the default properties assigned to a static route apply to all the next-hop addresses configured for the static route. If, however, you want to configure two possible next-hop addresses for a particular route and have them treated differently, you can define one as a qualified next hop.
Qualified next hops allow you to associate one or more properties with a particular next-hop address. You can set an overall preference for a particular static route and then specify a different preference for the qualified next hop.
First, let’s try without qualified next-hop.
amolak@R1# set routing-options static route 1.1.0.2/32 next-hop 1.1.21.2 preference 10
[edit]
amolak@R1# commit
commit complete
[edit]
amolak@R1# exit
Exiting configuration mode
amolak@R1> show route 1.1.0.2
inet.0: 6 destinations, 6 routes (6 active, 0 holddown, 0 hidden)
+ = Active Route, – = Last Active, * = Both
1.1.0.2/32 *[Static/10] 00:00:03
to 1.1.12.2 via em0.0
> to 1.1.21.2 via em1.0
It has changed the preference value to 10 for both the next-hop addresses.
Rollback this configuration. We will discuss rollback feature in some other post. In short, JunOS keeps last fifty configurations (0-49). 0 is the current configuration state number.
amolak@R1# rollback 1
load complete
[edit]
amolak@R1# show | compare
[edit routing-options static route 1.1.0.2/32]
– next-hop [ 1.1.12.2 1.1.21.2 ];
– preference 10;
+ next-hop 1.1.12.2;
[edit]
‘show | compare’ compares the current configuration and last committed configuration and shows the differences.
Now lets add a second static route with qualified next-hop.
amolak@R1# set routing-options static route 1.1.0.2/32 qualified-next-hop 1.1.21.2 preference 10
[edit]
amolak@R1# commit
commit complete
The router is using the routes via next-hop marked with asterisk sign.
[edit]
amolak@R1# run show route 1.1.0.2
inet.0: 6 destinations, 7 routes (6 active, 0 holddown, 0 hidden)
+ = Active Route, – = Last Active, * = Both
1.1.0.2/32 *[Static/5] 00:01:10
> to 1.1.12.2 via em0.0
[Static/10] 00:00:03
> to 1.1.21.2 via em1.0
[edit]
amolak@R1#
If we disable (admin shutdown) the interface em0, the R2′s loopback interface IP is reachable via other next-hop now.
amolak@R1# set interfaces em0 disable
[edit]
amolak@R1# commit
commit complete
[edit]
amolak@R1# run show route 1.1.0.2
inet.0: 5 destinations, 5 routes (5 active, 0 holddown, 0 hidden)
+ = Active Route, – = Last Active, * = Both
1.1.0.2/32 *[Static/10] 00:01:00
> to 1.1.21.2 via em1.0
[edit]
Activate em0 interface.
amolak@R1# delete interfaces em0 disable
[edit]
amolak@R1# commit
commit complete
[edit]
amolak@R1# run show route 1.1.0.2
inet.0: 6 destinations, 7 routes (6 active, 0 holddown, 0 hidden)
+ = Active Route, – = Last Active, * = Both
1.1.0.2/32 *[Static/5] 00:00:06
> to 1.1.12.2 via em0.0
[Static/10] 00:01:23
> to 1.1.21.2 via em1.0
[edit]
amolak@R1#
Similarly, Configure R2.
[edit]
amolak@R2# set routing-options static route 1.1.0.1/32 qualified-next-hop 1.1.12.1 preference 10
[edit]
amolak@R2# commit
commit complete
[edit]
amolak@R2# run show route 1.1.0.1
inet.0: 6 destinations, 7 routes (6 active, 0 holddown, 0 hidden)
+ = Active Route, – = Last Active, * = Both
1.1.0.1/32 *[Static/5] 02:39:56
> to 1.1.12.1 via em0.0
[Static/10] 00:00:04
> to 1.1.12.1 via em0.0
[edit]
amolak@R2#
Final configuration on both routers.
amolak@R1> show configuration
## Last commit: 2014-04-14 10:38:46 UTC by amolak
version 10.1R1.8;
system {
host-name R1;
root-authentication {
encrypted-password "$1$EhyKZlJc$0WIdzQaoqwKSMBe92FcGy/"; ## SECRET-DATA
}
login {
user amolak {
uid 2000;
class super-user;
authentication {
encrypted-password "$1$qNdbsrlc$Ha4nBWDuB6OdNpKzXIYZX1"; ## SECRET-DATA
}
}
}
syslog {
user * {
any emergency;
}
file messages {
any notice;
authorization info;
}
file interactive-commands {
interactive-commands any;
}
}
}
interfaces {
em0 {
unit 0 {
family inet {
address 1.1.12.1/24;
}
}
}
em1 {
unit 0 {
family inet {
address 1.1.21.1/24;
}
}
}
lo0 {
unit 0 {
family inet {
address 1.1.0.1/32;
}
}
}
}
routing-options {
static {
route 1.1.0.2/32 {
next-hop 1.1.12.2;
qualified-next-hop 1.1.21.2 {
preference 10;
}
}
}
}
amolak@R1>
amolak@R2> show configuration
## Last commit: 2014-04-14 13:06:44 UTC by amolak
version 10.1R1.8;
system {
host-name R2;
root-authentication {
encrypted-password "$1$2LOSmGiX$1ezYIzYSXOOfyvm15dz5S0"; ## SECRET-DATA
}
login {
user amolak {
uid 2000;
class super-user;
authentication {
encrypted-password "$1$pqvVkBia$MxnHYNRelBmY9IQ8MR.rn/"; ## SECRET-DATA
}
}
}
syslog {
user * {
any emergency;
}
file messages {
any notice;
authorization info;
}
file interactive-commands {
interactive-commands any;
}
}
}
interfaces {
em0 {
unit 0 {
family inet {
address 1.1.12.2/24;
}
}
}
em1 {
unit 0 {
family inet {
address 1.1.21.2/24;
}
}
}
lo0 {
unit 0 {
family inet {
address 1.1.0.2/32;
}
}
}
}
routing-options {
static {
route 1.1.0.1/32 {
next-hop 1.1.12.1;
qualified-next-hop 1.1.12.1 {
preference 10;
}
}
}
}
amolak@R2>